Download AWS Certified Security - Specialty.SCS-C02.ExamTopics.2025-12-05.306q.vcex
| Vendor: | Amazon |
| Exam Code: | SCS-C02 |
| Exam Name: | AWS Certified Security - Specialty |
| Date: | Dec 05, 2025 |
| File Size: | 3 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
A security engineer is configuring a new website that is named example.com. The security engineer wants to secure communications with the website by requiring users to connect to example.com through HTTPS.
Which of the following is a valid option for storing SSL/TLS certificates?
- Custom SSL certificate that is stored in AWS Key Management Service (AWS KMS)
- Default SSL certificate that is stored in Amazon CloudFront
- Custom SSL certificate that is stored in AWS Certificate Manager (ACM)
- Default SSL certificate that is stored in Amazon S3
Correct answer: C
Explanation:
C: 11 - Mosted C: 11 - Mosted
Question 2
A company is migrating one of its legacy systems from an on-premises data center to AWS. The application server will run on AWS, but the database must remain in the on-premises data center for compliance reasons. The database is sensitive to network latency. Additionally, the data that travels between the on-premises data center and AWS must have IPsec encryption.
Which combination of AWS solutions will meet these requirements? (Choose two.)
- AWS Site-to-Site VPN
- AWS Direct Connect
- AWS VPN CloudHub
- VPC peering
- NAT gateway
Correct answer: AB
Explanation:
AB: 10 - Mosted AB: 10 - Mosted
Question 3
A company has deployed Amazon GuardDuty and now wants to implement automation for potential threats. The company has decided to start with RDP brute force attacks that come from Amazon EC2 instances in the company's AWS environment. A security engineer needs to implement a solution that blocks the detected communication from a suspicious instance until investigation and potential remediation can occur.
Which solution will meet these requirements?
- Configure GuardDuty to send the event to an Amazon Kinesis data stream. Process the event with an Amazon Kinesis Data Analytics for Apache Flink application that sends a notification to the company through Amazon Simple Notification Service (Amazon SNS). Add rules to the network ACL to block traffic to and from the suspicious instance.
- Configure GuardDuty to send the event to Amazon EventBridge. Deploy an AWS WAF web ACL. Process the event with an AWS Lambda function that sends a notification to the company through Amazon Simple Notification Service (Amazon SNS) and adds a web ACL rule to block traffic to and from the suspicious instance.
- Enable AWS Security Hub to ingest GuardDuty findings and send the event to Amazon EventBridge. Deploy AWS Network Firewall. Process the event with an AWS Lambda function that adds a rule to a Network Firewall firewall policy to block traffic to and from the suspicious instance.
- Enable AWS Security Hub to ingest GuardDuty findings. Configure an Amazon Kinesis data stream as an event destination for Security Hub. Process the event with an AWS Lambda function that replaces the security group of the suspicious instance with a security group that does not allow any connections.
Correct answer: C
Explanation:
C: 27 - MostedD: 10 C: 27 - MostedD: 10
Question 4
Company A has an AWS account that is named Account A. Company A recently acquired Company B, which has an AWS account that is named Account B. Company B stores its files in an Amazon S3 bucket. The administrators need to give a user from Account A full access to the S3 bucket in Account B.
After the administrators adjust the IAM permissions for the user in Account A to access the S3 bucket in Account B, the user still cannot access any files in the S3 bucket.
Which solution will resolve this issue?
- In Account B, create a bucket ACL to allow the user from Account A to access the S3 bucket in Account B.
- In Account B, create an object ACL to allow the user from Account A to access all the objects in the S3 bucket in Account B.
- In Account B, create a bucket policy to allow the user from Account A to access the S3 bucket in Account B.
- In Account B, create a user policy to allow the user from Account A to access the S3 bucket in Account B.
Correct answer: C
Explanation:
C: 11 - Mosted C: 11 - Mosted
Question 5
A security engineer is working with a company to design an ecommerce application. The application will run on Amazon EC2 instances that run in an Auto Scaling group behind an Application Load Balancer (ALB). The application will use an Amazon RDS DB instance for its database.
The only required connectivity from the internet is for HTTP and HTTPS traffic to the application. The application must communicate with an external payment provider that allows traffic only from a preconfigured allow list of IP addresses. The company must ensure that communications with the external payment provider are not interrupted as the environment scales.
Which combination of actions should the security engineer recommend to meet these requirements? (Choose three.)
- Deploy a NAT gateway in each private subnet for every Availability Zone that is in use.
- Place the DB instance in a public subnet.
- Place the DB instance in a private subnet.
- Configure the Auto Scaling group to place the EC2 instances in a public subnet.
- Configure the Auto Scaling group to place the EC2 instances in a private subnet.
- Deploy the ALB in a private subnet.
Correct answer: ACE
Explanation:
ACD: 2ACE: 12 - MostedCE: 11 ACD: 2ACE: 12 - MostedCE: 11
Question 6
A company has a legacy application that runs on a single Amazon EC2 instance. A security audit shows that the application has been using an IAM access key within its code to access an Amazon S3 bucket that is named DOC-EXAMPLE-BUCKET1 in the same AWS account. This access key pair has the s3:GetObject permission to all objects in only this S3 bucket. The company takes the application offline because the application is not compliant with the company’s security policies for accessing other AWS resources from Amazon EC2.
A security engineer validates that AWS CloudTrail is turned on in all AWS Regions. CloudTrail is sending logs to an S3 bucket that is named DOC-EXAMPLE-BUCKET2. This S3 bucket is in the same AWS account as DOC-EXAMPLE-BUCKET1. However, CloudTrail has not been configured to send logs to Amazon CloudWatch Logs.
The company wants to know if any objects in DOC-EXAMPLE-BUCKET1 were accessed with the IAM access key in the past 60 days. If any objects were accessed, the company wants to know if any of the objects that are text files (.txt extension) contained personally identifiable information (PII).
Which combination of steps should the security engineer take to gather this information? (Choose two.)
- Use Amazon CloudWatch Logs Insights to identify any objects in DOC-EXAMPLE-BUCKET1 that contain PII and that were available to the access key.
- Use Amazon OpenSearch Service to query the CloudTrail logs in DOC-EXAMPLE-BUCKET2 for API calls that used the access key to access an object that contained PII.
- Use Amazon Athena to query the CloudTrail logs in DOC-EXAMPLE-BUCKET2 for any API calls that used the access key to access an object that contained PII.
- Use AWS Identity and Access Management Access Analyzer to identify any API calls that used the access key to access objects that contained PII in DOC-EXAMPLE-BUCKET1.
- Configure Amazon Macie to identify any objects in DOC-EXAMPLE-BUCKET1 that contain PII and that were available to the access key.
Correct answer: CE
Explanation:
C: 1CE: 16 - Mosted C: 1CE: 16 - Mosted
Question 7
While securing the connection between a company’s VPC and its on-premises data center, a security engineer sent a ping command from an on-premises host (IP address 203.0.113.12) to an Amazon EC2 instance (IP address 172.31.16.139). The ping command did not return a response. The flow log in the VPC showed the following:
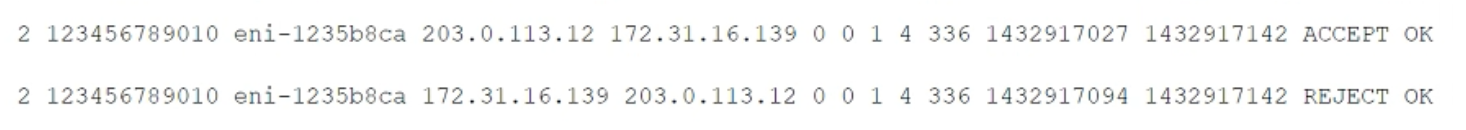
What action should be performed to allow the ping to work?
- In the security group of the EC2 instance, allow inbound ICMP traffic.
- In the security group of the EC2 instance, allow outbound ICMP traffic.
- In the VPC’s NACL, allow inbound ICMP traffic.
- In the VPC’s NACL, allow outbound ICMP traffic.
Correct answer: D
Explanation:
A: 1C: 1D: 12 - Mosted A: 1C: 1D: 12 - Mosted
Question 8
An international company has established a new business entity in South Korea. The company also has established a new AWS account to contain the workload for the South Korean region. The company has set up the workload in the new account in the ap-northeast-2 Region. The workload consists of three Auto Scaling groups of Amazon EC2 instances. All workloads that operate in this Region must keep system logs and application logs for 7 years.
A security engineer must implement a solution to ensure that no logging data is lost for each instance during scaling activities. The solution also must keep the logs for only the required period of 7 years.
Which combination of steps should the security engineer take to meet these requirements? (Choose three.)
- Ensure that the Amazon CloudWatch agent is installed on all the EC2 instances that the Auto Scaling groups launch. Generate a CloudWatch agent configuration file to forward the required logs to Amazon CloudWatch Logs.
- Set the log retention for desired log groups to 7 years.
- Attach an IAM role to the launch configuration or launch template that the Auto Scaling groups use. Configure the role to provide the necessary permissions to forward logs to Amazon CloudWatch Logs.
- Attach an IAM role to the launch configuration or launch template that the Auto Scaling groups use. Configure the role to provide the necessary permissions to forward logs to Amazon S3.
- Ensure that a log forwarding application is installed on all the EC2 instances that the Auto Scaling groups launch. Configure the log forwarding application to periodically bundle the logs and forward the logs to Amazon S3.
- Configure an Amazon S3 Lifecycle policy on the target S3 bucket to expire objects after 7 years.
Correct answer: ABC
Explanation:
ABC: 9 - MostedACF: 3 ABC: 9 - MostedACF: 3
Question 9
A company is designing a multi-account structure for its development teams. The company is using AWS Organizations and AWS IAM Identity Center (AWS Single Sign-On). The company must implement a solution so that the development teams can use only specific AWS Regions and so that each AWS account allows access to only specific AWS services.
Which solution will meet these requirements with the LEAST operational overhead?
- Use IAM Identity Center to set up service-linked roles with IAM policy statements that include the Condition, Resource, and NotAction elements to allow access to only the Regions and services that are needed.
- Deactivate AWS Security Token Service (AWS STS) in Regions that the developers are not allowed to use.
- Create SCPs that include the Condition, Resource, and NotAction elements to allow access to only the Regions and services that are needed.
- For each AWS account, create tailored identity-based policies for IAM Identity Center. Use statements that include the Condition, Resource, and NotAction elements to allow access to only the Regions and services that are needed.
Correct answer: C
Explanation:
A: 2C: 8 - Mosted A: 2C: 8 - Mosted
Question 10
A company is developing an ecommerce application. The application uses Amazon EC2 instances and an Amazon RDS MySQL database. For compliance reasons, data must be secured in transit and at rest. The company needs a solution that minimizes operational overhead and minimizes cost.
Which solution meets these requirements?
- Use TLS certificates from AWS Certificate Manager (ACM) with an Application Load Balancer. Deploy self-signed certificates on the EC2 instances. Ensure that the database client software uses a TLS connection to Amazon RDS. Enable encryption of the RDS DB instance. Enable encryption on the Amazon Elastic Block Store (Amazon EBS) volumes that support the EC2 instances.
- Use TLS certificates from a third-party vendor with an Application Load Balancer. Install the same certificates on the EC2 instances. Ensure that the database client software uses a TLS connection to Amazon RDS. Use AWS Secrets Manager for client-side encryption of application data.
- Use AWS CloudHSM to generate TLS certificates for the EC2 instances. Install the TLS certificates on the EC2 instances. Ensure that the database client software uses a TLS connection to Amazon RDS. Use the encryption keys from CloudHSM for client-side encryption of application data.
- Use Amazon CloudFront with AWS WAF. Send HTTP connections to the origin EC2 instances. Ensure that the database client software uses a TLS connection to Amazon RDS. Use AWS Key Management Service (AWS KMS) for client-side encryption of application data before the data is stored in the RDS database.
Correct answer: A
Explanation:
A: 12 - Mosted A: 12 - Mosted
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



