Download Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS).200-201.ExamTopics.2025-08-09.321q.tqb
| Vendor: | Cisco |
| Exam Code: | 200-201 |
| Exam Name: | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) |
| Date: | Aug 09, 2025 |
| File Size: | 21 MB |
How to open TQB files?
Files with TQB (Taurus Question Bank) extension can be opened by Taurus Exam Studio.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
What are two categories of DDoS attacks? (Choose two.)
- direct
- reflected
- split brain
- scanning
- phishing
Correct answer: AB
Explanation:
AB: 5 - Mosted AB: 5 - Mosted
Question 2
The SOC team has confirmed a potential indicator of compromise on an isolated endpoint. The team has narrowed the potential malware type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling the event?
- Perform an AV scan on the infected endpoint.
- Isolate the infected endpoint from the network.
- Prioritize incident handling based on the impact.
- Analyze the malware behavior.
Correct answer: D
Explanation:
B: 4C: 1D: 12 - Mosted B: 4C: 1D: 12 - Mosted
Question 3
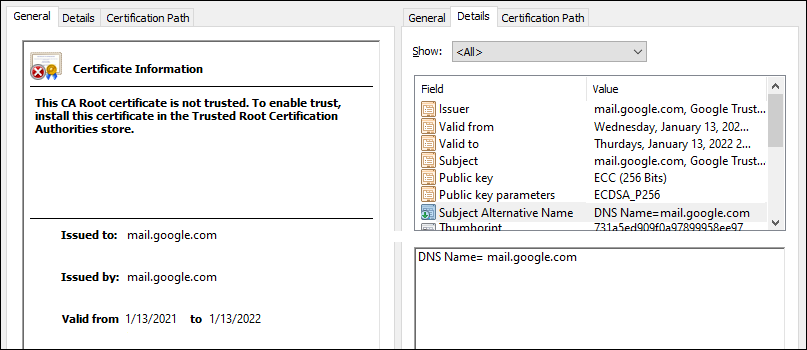
Refer to the exhibit. A company employee is connecting to mail.google.com from an endpoint device. The website is loaded but with an error. What is occurring?
- man-in-the-middle attack
- Certificate is not in trusted roots.
- DNS hijacking attack.
- Endpoint local time is invalid.
Correct answer: B
Explanation:
B: 3 - Mosted B: 3 - Mosted
Question 4
What is the difference between deep packet inspection and stateful inspection?
- Stateful inspection is more secure due to its complex signatures, and deep packet inspection requires less human intervention.
- Deep packet inspection is more secure due to its complex signatures, and stateful inspection requires less human intervention.
- Deep packet inspection gives insights up to Layer 7, and stateful inspection gives insights only up to Layer 4.
- Stateful inspection verifies data at the transport layer, and deep packet inspection verifies data at the application layer.
Correct answer: C
Explanation:
C: 4 - MostedD: 2 C: 4 - MostedD: 2
Question 5
How does agentless monitoring differ from agent-based monitoring?
- Agentless can access the data via API, while agent-based uses a less efficient method and accesses log data through WMI.
- Agent-based monitoring has a lower initial cost for deployment, while agentless requires resource-intensive deployment.
- Agent-based monitoring is less intrusive in gathering log data, while agentless requires open ports to fetch the logs.
- Agent-based has a possibility to locally filter and transmit only valuable data, while agentless has much higher network utilization.
Correct answer: D
Explanation:
C: 1D: 6 - Mosted C: 1D: 6 - Mosted
Question 6
What is the difference between inline traffic interrogation and traffic mirroring?
- Inline replicates the traffic to preserve integrity rather than modifying packets before sending them to other analysis tools.
- Traffic mirroring results in faster traffic analysis and inline is considerably slower due to latency.
- Inline interrogation is less complex as traffic mirroring applies additional tags to data.
- Traffic mirroring copies the traffic rather than forwarding it directly to the analysis tools.
Correct answer: D
Explanation:
D: 4 - Mosted D: 4 - Mosted
Question 7
What is threat hunting?
- Focusing on proactively detecting possible signs of intrusion and compromise.
- Managing a vulnerability assessment report to mitigate potential threats.
- Attempting to deliberately disrupt servers by altering their availability.
- Pursuing competitors and adversaries to infiltrate their system to acquire intelligence data.
Correct answer: A
Explanation:
A: 1 - Mosted A: 1 - Mosted
Question 8
According to the September 2020 threat intelligence feeds, a new malware called Egregor was introduced and used in many attacks. Distribution of Egregor is primarily through a Cobalt Strike that has been installed on victim's workstations using RDP exploits. Malware exfiltrates the victim's data to a command and control server. The data is used to force victims pay or lose it by publicly releasing it. Which type of attack is described?
- malware attack
- insider threat
- ransomware attack
- whale-phishing
Correct answer: C
Explanation:
C: 3 - Mosted C: 3 - Mosted
Question 9
How does TOR alter data content during transit?
- It encrypts content and destination information over multiple layers.
- It traverses source traffic through multiple destinations before reaching the receiver.
- It redirects destination traffic through multiple sources avoiding traceability.
- It spoofs the destination and source information protecting both sides.
Correct answer: A
Explanation:
A: 3 - MostedC: 1 A: 3 - MostedC: 1
Question 10
Which information must an organization use to understand the threats currently targeting the organization?
- vendor suggestions
- threat intelligence
- risk scores
- vulnerability exposure
Correct answer: B
Explanation:
B: 1 - Mosted B: 1 - Mosted
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



