Download Cisco Meraki Solutions Specialist.500-220.ExamTopics.2025-12-28.85q.tqb
| Vendor: | Cisco |
| Exam Code: | 500-220 |
| Exam Name: | Cisco Meraki Solutions Specialist |
| Date: | Dec 28, 2025 |
| File Size: | 2 MB |
How to open TQB files?
Files with TQB (Taurus Question Bank) extension can be opened by Taurus Exam Studio.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
Which Radio Frequency (RF) Profile setting is typically used to decrease the Service Set Identifier (SSID) overhead, exclude legacy clients, and promote more efficient client roaming?
- Minimum bitrate
- Channel width
- Band selection
- Transmit power range
Correct answer: A
Question 2
Which two limitations are addressed by the implementation of Adaptive Policy? (Choose two.)
- managing network policies when IP addresses are prone to changes over time
- applying segmentation inside a VLAN
- preventing the micro-segmentation of clients within the network
- ensuring dedicated bandwidth for specific applications
- implementing Quality of Service (QoS) policies within a flat Layer 2 network
Correct answer: AB
Question 3
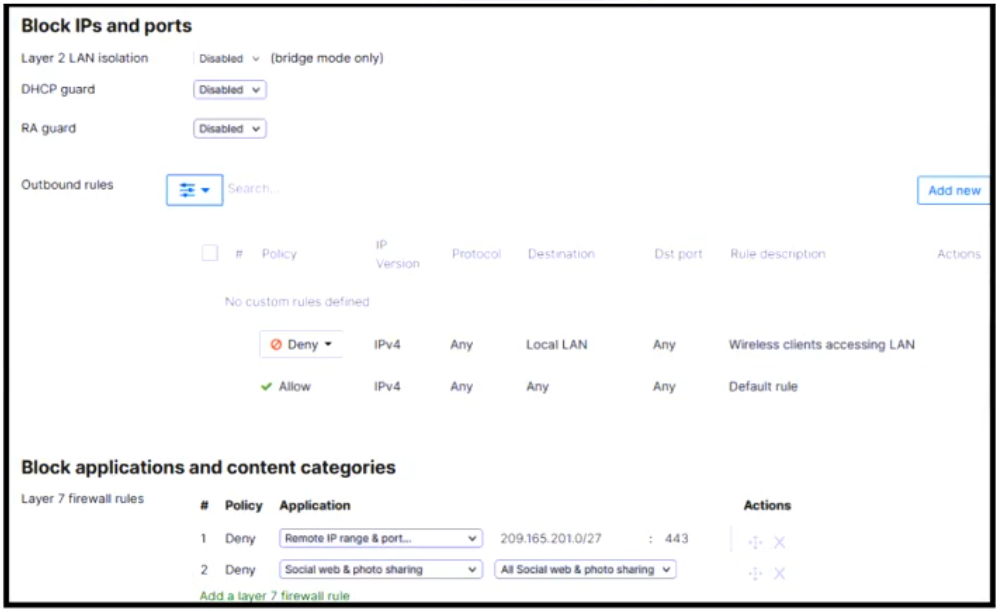
Refer to the exhibit. After associating with the Officers SSID and receiving an IP address on the 10.0.0/8 subnet, a wireless user submitted a support ticket that they cannot access wired network resources. Which configuration will provide successful network communication?
- The ‘DHCP guard’ setting should be adjusted from ‘Disabled’ to ‘Enabled.’
- The Layer 7 firewall rules prevent wired IP traffic from being forwarded and should be disabled.
- An ‘Allow’ rule must be added to the Outbound rules list to connect to the necessary resources.
- The Layer 2 LAN isolation setting should be adjusted from ‘Disabled’ to ‘Enabled.’
Correct answer: C
Question 4
A legacy wireless client, supporting WPA2 security, cannot associate to a guest wireless network. What is the cause?
- The guest wireless network is configured with layer 2 LAN isolation.
- The guest wireless network is configured with Open (no encryption).
- The guest wireless network is configured with WPA3 transition mode with 802.1w set to “Enabled.”
- The guest wireless network is configured with Opportunistic Wireless Encryption (OWE) with 802.1w set to “Required.”
Correct answer: D
Question 5
Which technique is not a PCI requirement but is considered a best practice for limiting the cardholder data environment (CDE) from the remainder of a corporate network?
- Limit inbound connections to the CDE while allowing all outbound connections originating from the CDE.
- Establishing wired network segmentation between the CDE and the rest of the corporate network.
- Implementing identical firewall rules between corporate and CDE egress points.
- Incorporate the CDE within the corporate network's established Demilitarized Zone (DMZ).
Correct answer: B
Question 6
Which two features can be configured on a Cisco Meraki MX security appliance and on a vMX virtual instance? (Choose two.)
- SD-WAN policies
- client VPN
- Active Directory
- Layer 3 and Layer 7 firewall rules
- threat protection
Correct answer: AD
Question 7
Which two wireless threats can be automatically mitigated by the dedicated security radio when using Air Marshal? (Choose two.)
- Malicious broadcasts
- Packet floods
- Network impersonation
- Wired LAN compromise
- SSID spoofing
Correct answer: BC
Question 8
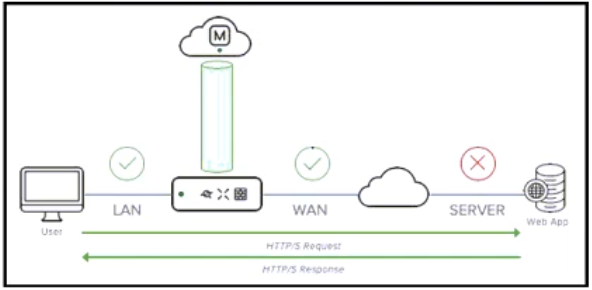
Refer to the exhibit. Meraki Insight aggregates network statistics on the MX and sends those aggregates back to the Meraki Cloud. In which three ways are aggregated statistics sent? (Choose three.)
- 443
- UDP
- TCP
- 7351
- SYSLOG traffic
- TLS-SYSLOG traffic
Correct answer: A
Question 9
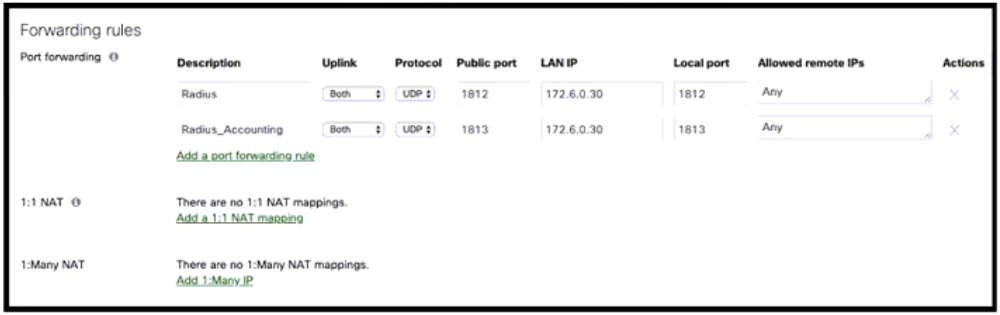
Refer to the exhibit. 172.16.0.0/24 is a configured local VLAN on the Cisco Meraki MX security appliance. What happens to inbound traffic flow to the MX WAN with a destination of TCP port 1813?
- The traffic is forwarded to 172.16.0.30 on the WAN.
- The traffic is dropped on the WAN of the MX security appliance.
- The traffic is forwarded to 172.16.0.30 on the LAN.
- The traffic is dropped on the WAN of the MX security appliance due to the “any” allow remote IP rule.
Correct answer: B
Question 10
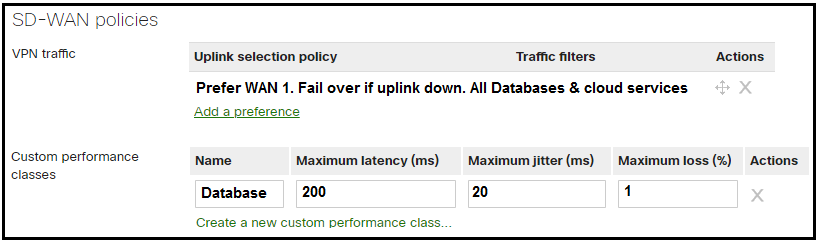
Refer to the exhibit. Which condition or conditions will cause the “All Databases & cloud services” SD-WAN traffic to be routed via a VPN tunnel on WAN2?
- WAN1 tunnel latency is 20 ms or more, irrespective of WAN2 tunnel performance.
- WAN1 tunnel latency is 20 ms or more, and WAN2 tunnel meets the configured performance criteria.
- WAN1 tunnel latency is 20 ms or less, irrespective of WAN2 tunnel performance.
- WAN1 tunnel latency is 20 ms or less, and WAN2 tunnel meets the configured performance criteria.
Correct answer: B
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



