Download CompTIA Advanced Security Practitioner-CASP-CAS-004.CAS-004.ExamTopics.2025-06-11.629q.tqb
| Vendor: | CompTIA |
| Exam Code: | CAS-004 |
| Exam Name: | CompTIA Advanced Security Practitioner-CASP-CAS-004 |
| Date: | Jun 11, 2025 |
| File Size: | 8 MB |
How to open TQB files?
Files with TQB (Taurus Question Bank) extension can be opened by Taurus Exam Studio.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
An organization is referencing NIST best practices for BCP creation while reviewing current internal organizational processes for mission-essential items.
Which of the following phases establishes the identification and prioritization of critical systems and functions?
- Review a recent gap analysis.
- Perform a cost-benefit analysis.
- Conduct a business impact analysis.
- Develop an exposure factor matrix.
Correct answer: C
Question 2
An organization is implementing a new identity and access management architecture with the following objectives:
- Supporting MFA against on-premises infrastructure
- Improving the user experience by integrating with SaaS applications
- Applying risk-based policies based on location
- Performing just-in-time provisioning
Which of the following authentication protocols should the organization implement to support these requirements?
- Kerberos and TACACS
- SAML and RADIUS
- OAuth and OpenID
- OTP and 802.1X
Correct answer: C
Question 3
A security analyst observes the following while looking through network traffic in a company's cloud log:
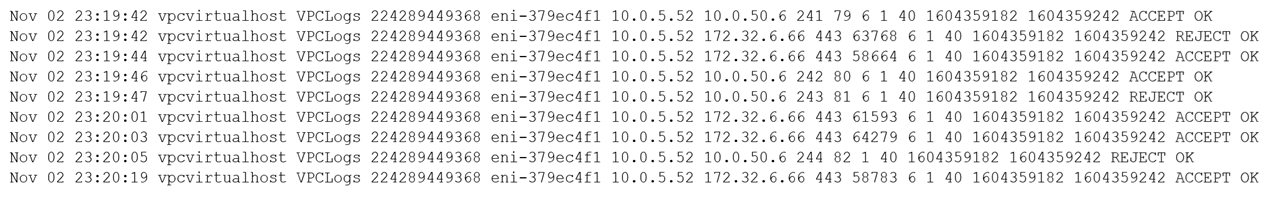
Which of the following steps should the security analyst take FIRST?
- Quarantine 10.0.5.52 and run a malware scan against the host.
- Access 10.0.5.52 via EDR and identify processes that have network connections.
- Isolate 10.0.50.6 via security groups.
- Investigate web logs on 10.0.50.6 to determine if this is normal traffic.
Correct answer: B
Question 4
Which of the following is the MOST important cloud-specific risk from the CSP's viewpoint?
- Isolation control failure
- Management plane breach
- Insecure data deletion
- Resource exhaustion
Correct answer: B
Question 5
An organization is developing a disaster recovery plan that requires data to be backed up and available at a moment's notice.
Which of the following should the organization consider FIRST to address this requirement?
- Implement a change management plan to ensure systems are using the appropriate versions.
- Hire additional on-call staff to be deployed if an event occurs.
- Design an appropriate warm site for business continuity.
- Identify critical business processes and determine associated software and hardware requirements.
Correct answer: D
Question 6
Leveraging cryptographic solutions to protect data that is in use ensures the data is encrypted:
- when it is passed across a local network.
- in memory during processing
- when it is written to a system's solid-state drive.
- by an enterprise hardware security module.
Correct answer: B
Question 7
A Chief Information Officer (CIO) wants to implement a cloud solution that will satisfy the following requirements:
- Support all phases of the SDLC.
- Use tailored website portal software.
- Allow the company to build and use its own gateway software.
- Utilize its own data management platform.
- Continue using agent-based security tools.
Which of the following cloud-computing models should the CIO implement?
- SaaS
- PaaS
- MaaS
- IaaS
Correct answer: B
Question 8
A security analyst detected a malicious PowerShell attack on a single server. The malware used the Invoke-Expression function to execute an external malicious script. The security analyst scanned the disk with an antivirus application and did not find any IOCs. The security analyst now needs to deploy a protection solution against this type of malware.
Which of the following BEST describes the type of malware the solution should protect against?
- Worm
- Logic bomb
- Fileless
- Rootkit
Correct answer: C
Question 9
A development team created a mobile application that contacts a company's back-end APIs housed in a PaaS environment. The APIs have been experiencing high processor utilization due to scraping activities. The security engineer needs to recommend a solution that will prevent and remedy the behavior.
Which of the following would BEST safeguard the APIs? (Choose two.)
- Bot protection
- OAuth 2.0
- Input validation
- Autoscaling endpoints
- Rate limiting
- CSRF protection
Correct answer: AE
Question 10
An organization's existing infrastructure includes site-to-site VPNs between datacenters. In the past year, a sophisticated attacker exploited a zero-day vulnerability on the VPN concentrator. Consequently, the Chief Information Security Officer (CISO) is making infrastructure changes to mitigate the risk of service loss should another zero-day exploit be used against the VPN solution.
Which of the following designs would be BEST for the CISO to use?
- Adding a second redundant layer of alternate vendor VPN concentrators
- Using Base64 encoding within the existing site-to-site VPN connections
- Distributing security resources across VPN sites
- Implementing IDS services with each VPN concentrator
- Transitioning to a container-based architecture for site-based services
Correct answer: A
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



