Download CompTIA SecurityX Certification.CAS-005.ExamTopics.2025-06-10.80q.vcex
| Vendor: | CompTIA |
| Exam Code: | CAS-005 |
| Exam Name: | CompTIA SecurityX Certification |
| Date: | Jun 10, 2025 |
| File Size: | 523 KB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
A security engineer is reviewing event logs because an employee successfully connected a personal Windows laptop to the corporate network, which is against company policy. Company policy allows all Windows 10 and 11 laptops to connect to the system as long as the MDM agent installed by IT is running. Only compliant devices can connect, and the logic in the system to evaluate compliant laptops is as follows:
Which of the following most likely occurred when the employee connected a personally owned Windows laptop and was allowed on the network?
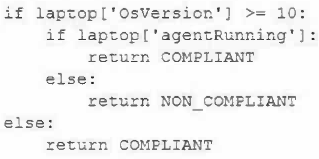
- The agent was not running on the laptop, which triggered a false positive.
- The OS was a valid version, but the MDM agent was not installed, triggering a true positive.
- The OS was running a Windows version below 10 and triggered a false negative.
- The OS version was higher than 11, and the MDM agent was running, triggering a true negative.
Correct answer: C
Question 2
Which of the following security features do email signatures provide?
- Non-repudiation
- Body encryption
- Code signing
- Sender authentication
- Chain of custody
Correct answer: A
Question 3
A software development company wants to ensure that users can confirm the software is legitimate when installing it. Which of the following is the best way for the company to achieve this security objective?
- Code signing
- Non-repudiation
- Key escrow
- Private keys
Correct answer: A
Question 4
While performing mandatory monthly patch updates on a production application server, the security analyst reports an instance of buffer overflow for a new application that was migrated to the cloud and is also publicly exposed. Security policy requires that only internal users have access to the application. Which of the following should the analyst implement to mitigate the issues reported? (Choose two.)
- Configure firewall rules to block all external traffic.
- Enable input validation for all fields.
- Enable automatic updates to be installed on all servers.
- Configure the security group to enable external traffic.
- Set up a DLP policy to alert for exfiltration on all application servers.
- Enable nightly vulnerability scans.
Correct answer: AB
Question 5
PKI can be used to support security requirements in the change management process. Which of the following capabilities does PKI provide for messages?
- Non-repudiation
- Confidentiality
- Delivery receipts
- Attestation
Correct answer: A
Question 6
Several unlabeled documents in a cloud document repository contain cardholder information. Which of the following configuration changes should be made to the DLP system to correctly label these documents in the future?
- Digital rights management
- Network traffic decryption
- Regular expressions
- Watermarking
Correct answer: C
Question 7
A systems administrator at a web-hosting provider has been tasked with renewing the public certificates of all customer sites. Which of the following would best support multiple domain names while minimizing the amount of certificates needed?
- OCSP
- CRL
- SAND. CA
Correct answer: C
Question 8
Which of the following best explain why organizations prefer to utilize code that is digitally signed? (Choose two.)
- It provides origin assurance.
- It verifies integrity.
- It provides increased confidentiality.
- It integrates with DRMs.
- It verifies the recipient's identity.
- It ensures the code is free of malware.
Correct answer: AB
Question 9
A security engineer receives reports through the organization's bug bounty program about remote code execution in a specific component in a custom application. Management wants to properly secure the component and proactively avoid similar issues. Which of the following is the best approach to uncover additional vulnerable paths in the application?
- Leverage an exploitation framework to uncover vulnerabilities.
- Use fuzz testing to uncover potential vulnerabilities in the application.
- Utilize a software composition analysis tool to report known vulnerabilities.
- Reverse engineer the application to look for vulnerable code paths.
- Analyze the use of an HTTP intercepting proxy to dynamically uncover issues.
Correct answer: B
Question 10
An ISAC supplied recent threat intelligence information about pictures used on social media that provide reconnaissance of systems in use in secure facilities. In response, the Chief Information Security Officer (CISO) wants several configuration changes implemented via the MDM to ensure the following:
- Camera functions and location services are blocked for corporate mobile devices.
- All social media is blocked on the corporate and guest wireless networks.
Which of the following is the CISO practicing to safeguard against the threat?
- Adversary emulation
- Operational security
- Open-source intelligence
- Social engineering
Correct answer: B
Question 11
A programmer is reviewing the following proprietary piece of code that was identified as a vulnerability due to users being authenticated when they provide incorrect credentials:
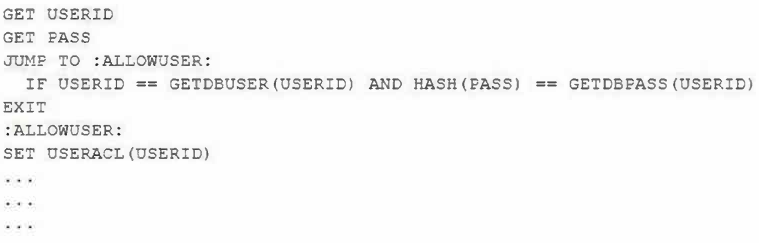
Which of the following should the programmer implement to remediate the code vulnerability?
- Salted hashing via the proprietary SHASH function
- Input validation in the first two lines of code
- Atomic execution of subroutines
- TOCTOU remediation in SET USERACL
- Database connection over encrypted channels
Correct answer: B
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



