Download CompTIA CSA+.CS0-003.DumpsMate.2025-07-02.362q.vcex
| Vendor: | CompTIA |
| Exam Code: | CS0-003 |
| Exam Name: | CompTIA CSA+ |
| Date: | Jul 02, 2025 |
| File Size: | 16 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
Which of the following would a security analyst most likely use to compare TTPs between different known adversaries of an organization?
- MITRE ATTACK
- Cyber Kill Cham
- OWASP
- STIXTAXII
Correct answer: A
Explanation:
MITRE ATT&CK is a framework and knowledge base that describes the tactics, techniques, and procedures (TTPs) used by various adversaries in cyberattacks. MITRE ATT&CK can help security analysts compare TTPs between different known adversaries of an organization, as well as identify patterns, gaps, or trends in adversary behavior. MITRE ATT&CK can also help security analysts improve threat detection, analysis, and response capabilities, as well as share threat intelligence with other organizations or communities MITRE ATT&CK is a framework and knowledge base that describes the tactics, techniques, and procedures (TTPs) used by various adversaries in cyberattacks. MITRE ATT&CK can help security analysts compare TTPs between different known adversaries of an organization, as well as identify patterns, gaps, or trends in adversary behavior. MITRE ATT&CK can also help security analysts improve threat detection, analysis, and response capabilities, as well as share threat intelligence with other organizations or communities
Question 2
A security analyst is reviewing the logs of a web server and notices that an attacker has attempted to exploit a SQL injection vulnerability.
Which of the following tools can the analyst use to analyze the attack and prevent future attacks?
- A web application firewall
- A network intrusion detection system
- A vulnerability scanner
- A web proxy
Correct answer: A
Explanation:
A web application firewall (WAF) is a tool that can protect web servers from attacks such as SQL injection, cross-site scripting, and other web-based threats. A WAF can filter, monitor, and block malicious HTTP traffic before it reaches the web server. A WAF can also be configured with rules and policies to detect and prevent specific types of attacks.References: CompTIA CySA+ Study Guide: Exam CS0-002, 2nd Edition, Chapter 3, “Security Architecture and Tool Sets”, page 91; CompTIA CySA+ Certification Exam Objectives Version 4.0, Domain 1.0 “Threat and Vulnerability Management”, Objective 1.2 “Given a scenario, analyze the results of a network reconnaissance”, Sub-objective “Web application attacks”, page 9CompTIA CySA+ Study Guide: Exam CS0-002, 2nd Edition : CompTIA CySA+ Certification Exam Objectives Version 4.0.pdf) A web application firewall (WAF) is a tool that can protect web servers from attacks such as SQL injection, cross-site scripting, and other web-based threats. A WAF can filter, monitor, and block malicious HTTP traffic before it reaches the web server. A WAF can also be configured with rules and policies to detect and prevent specific types of attacks.
References: CompTIA CySA+ Study Guide: Exam CS0-002, 2nd Edition, Chapter 3, “Security Architecture and Tool Sets”, page 91; CompTIA CySA+ Certification Exam Objectives Version 4.0, Domain 1.0 “Threat and Vulnerability Management”, Objective 1.2 “Given a scenario, analyze the results of a network reconnaissance”, Sub-objective “Web application attacks”, page 9
CompTIA CySA+ Study Guide: Exam CS0-002, 2nd Edition : CompTIA CySA+ Certification Exam Objectives Version 4.0.pdf)
Question 3
The Chief Executive Officer (CEO) has notified that a confidential trade secret has been compromised.
Which of the following communication plans should the CEO initiate?
- Alert department managers to speak privately with affected staff.
- Schedule a press release to inform other service provider customers of the compromise.
- Disclose to all affected parties in the Chief Operating Officer for discussion and resolution.
- Verify legal notification requirements of PII and SPII in the legal and human resource departments.
Correct answer: A
Explanation:
The CEO should initiate an alert to department managers to speak privately with affected staff. This is because the trade secret is confidential and should not be disclosed to the public. Additionally, the CEO should verify legal notification requirements of PII and SPII in the legal and human resource departments to ensure compliance with data protection laws.References: CompTIA CySA+ Study Guide: Exam CS0-002, 2nd Edition, Chapter 4, “Data Protection and Privacy Practices”, page 194; CompTIA CySA+ Certification Exam Objectives Version 4.0, Domain 4.0 “Compliance and Assessment”, Objective 4.1 “Given a scenario, analyze data as part of a security incident”, Sub-objective “Data classification levels”, page 23 The CEO should initiate an alert to department managers to speak privately with affected staff. This is because the trade secret is confidential and should not be disclosed to the public. Additionally, the CEO should verify legal notification requirements of PII and SPII in the legal and human resource departments to ensure compliance with data protection laws.
References: CompTIA CySA+ Study Guide: Exam CS0-002, 2nd Edition, Chapter 4, “Data Protection and Privacy Practices”, page 194; CompTIA CySA+ Certification Exam Objectives Version 4.0, Domain 4.0 “Compliance and Assessment”, Objective 4.1 “Given a scenario, analyze data as part of a security incident”, Sub-objective “Data classification levels”, page 23
Question 4
An organization conducted a web application vulnerability assessment against the corporate website, and the following output was observed:
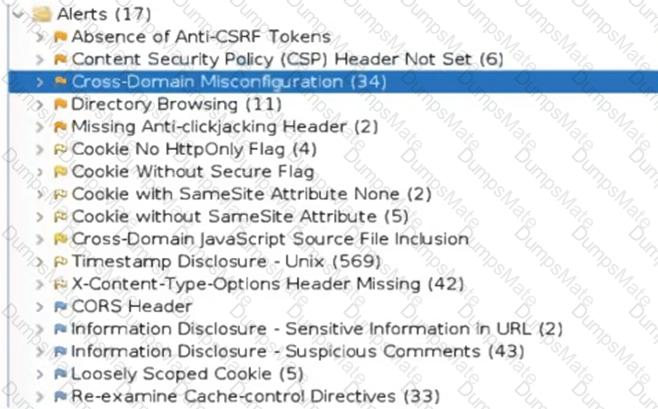
Which of the following tuning recommendations should the security analyst share?
- Set an HttpOnlvflaq to force communication by HTTPS
- Block requests without an X-Frame-Options header
- Configure an Access-Control-Allow-Origin header to authorized domains
- Disable the cross-origin resource sharing header
Correct answer: B
Explanation:
The output shows that the web application is vulnerable to clickjacking attacks, which allow an attacker to overlay a hidden frame on top of a legitimate page and trick users into clicking on malicious links. Blocking requests without an X-Frame-Options header can prevent this attack by instructing the browser to not display the page within a frame. The output shows that the web application is vulnerable to clickjacking attacks, which allow an attacker to overlay a hidden frame on top of a legitimate page and trick users into clicking on malicious links. Blocking requests without an X-Frame-Options header can prevent this attack by instructing the browser to not display the page within a frame.
Question 5
A new cybersecurity analyst is tasked with creating an executive briefing on possible threats to the organization.
Which of the following will produce the data needed for the briefing?
- Firewall logs
- Indicators of compromise
- Risk assessment
- Access control lists
Correct answer: B
Explanation:
Indicators of compromise (IoCs) are pieces of data or evidence that suggest a system or network has been compromised by an attacker or malware. IoCs can include IP addresses, domain names, URLs, file hashes, registry keys, network traffic patterns, user behaviors, or system anomalies. IoCs can be used to detect, analyze, and respond to security incidents, as well as to share threat intelligence with other organizations or authorities. IoCs can produce the data needed for an executive briefing on possible threats to the organization, as they can provide information on the source, nature, scope, impact, and mitigation of the threats. Indicators of compromise (IoCs) are pieces of data or evidence that suggest a system or network has been compromised by an attacker or malware. IoCs can include IP addresses, domain names, URLs, file hashes, registry keys, network traffic patterns, user behaviors, or system anomalies. IoCs can be used to detect, analyze, and respond to security incidents, as well as to share threat intelligence with other organizations or authorities. IoCs can produce the data needed for an executive briefing on possible threats to the organization, as they can provide information on the source, nature, scope, impact, and mitigation of the threats.
Question 6
A security analyst needs to mitigate a known, exploited vulnerability related not tack vector that embeds software through the USB interface.
Which of the following should the analyst do first?
- Conduct security awareness training on the risks of using unknown and unencrypted USBs.
- Write a removable media policy that explains that USBs cannot be connected to a company asset.
- Check configurations to determine whether USB ports are enabled on company assets.
- Review logs to see whether this exploitable vulnerability has already impacted the company.
Correct answer: C
Explanation:
USB ports are a common attack vector that can be used to deliver malware, steal data, or compromise systems. The first step to mitigate this vulnerability is to check the configurations of the company assets and disable or restrict the USB ports if possible. This will prevent unauthorized devices from being connected and reduce the attack surface. The other options are also important, but they are not the first priority in this scenario.References:CompTIA CySA+ CS0-003 Certification Study Guide, page 247What are Attack Vectors: Definition & Vulnerabilities, section “How to secure attack vectors”Are there any attack vectors for a printer connected through USB in a Windows environment?, answer by user “schroeder” USB ports are a common attack vector that can be used to deliver malware, steal data, or compromise systems. The first step to mitigate this vulnerability is to check the configurations of the company assets and disable or restrict the USB ports if possible. This will prevent unauthorized devices from being connected and reduce the attack surface. The other options are also important, but they are not the first priority in this scenario.
References:
- CompTIA CySA+ CS0-003 Certification Study Guide, page 247
- What are Attack Vectors: Definition & Vulnerabilities, section “How to secure attack vectors”
- Are there any attack vectors for a printer connected through USB in a Windows environment?, answer by user “schroeder”
Question 7
A company that has a geographically diverse workforce and dynamic IPs wants to implement a vulnerability scanning method with reduced network traffic.
Which of the following would best meet this requirement?
- External
- Agent-based
- Non-credentialed
- Credentialed
Correct answer: B
Explanation:
Agent-based vulnerability scanning is a method that involves installing software agents on the target systems or networks that can perform local scans and report the results to a central server or console. Agent-based vulnerability scanning can reduce network traffic, as the scans are performed locally and only the results are transmitted over the network. Agent-based vulnerability scanning can also provide more accurate and up-to-date results, as the agents can scan continuously or on-demand, regardless of the system or network status or location. Agent-based vulnerability scanning is a method that involves installing software agents on the target systems or networks that can perform local scans and report the results to a central server or console. Agent-based vulnerability scanning can reduce network traffic, as the scans are performed locally and only the results are transmitted over the network. Agent-based vulnerability scanning can also provide more accurate and up-to-date results, as the agents can scan continuously or on-demand, regardless of the system or network status or location.
Question 8
Following a recent security incident, the Chief Information Security Officer is concerned with improving visibility and reporting of malicious actors in the environment. The goal is to reduce the time to prevent lateral movement and potential data exfiltration. Which of the following techniques will best achieve the improvement?
- Mean time to detect
- Mean time to respond
- Mean time to remediate
- Service-level agreement uptime
Correct answer: A
Explanation:
Mean time to detect (MTTD) is a metric that measures how quickly an organization can identify a security incident or a malicious actor in the environment. Reducing MTTD can improve visibility and reporting of threats, as well as prevent lateral movement and data exfiltration by detecting them sooner. Mean time to detect (MTTD) is a metric that measures how quickly an organization can identify a security incident or a malicious actor in the environment. Reducing MTTD can improve visibility and reporting of threats, as well as prevent lateral movement and data exfiltration by detecting them sooner.
Question 9
You are a penetration tester who is reviewing the system hardening guidelines for a company. Hardening guidelines indicate the following.
- There must be one primary server or service per device.
- Only default port should be used
- Non- secure protocols should be disabled.
- The corporate internet presence should be placed in a protected subnet
Instructions :
- Using the available tools, discover devices on the corporate network and the services running on these devices.
- You must determine
- ip address of each device
- The primary server or service each device
- The protocols that should be disabled based on the hardening guidelines
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Answer below images Answer below images
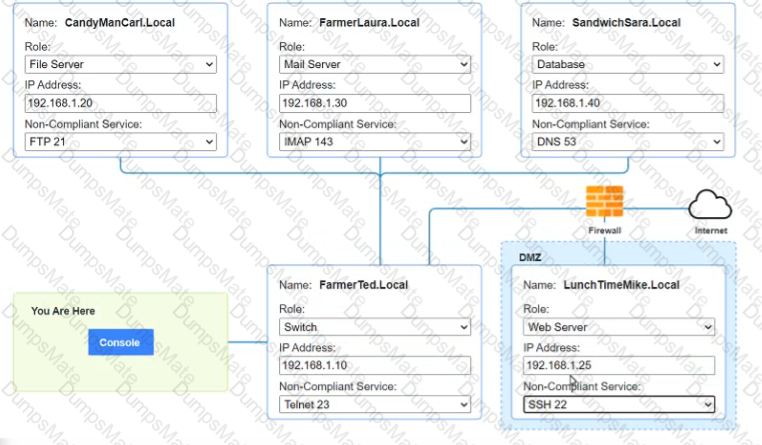
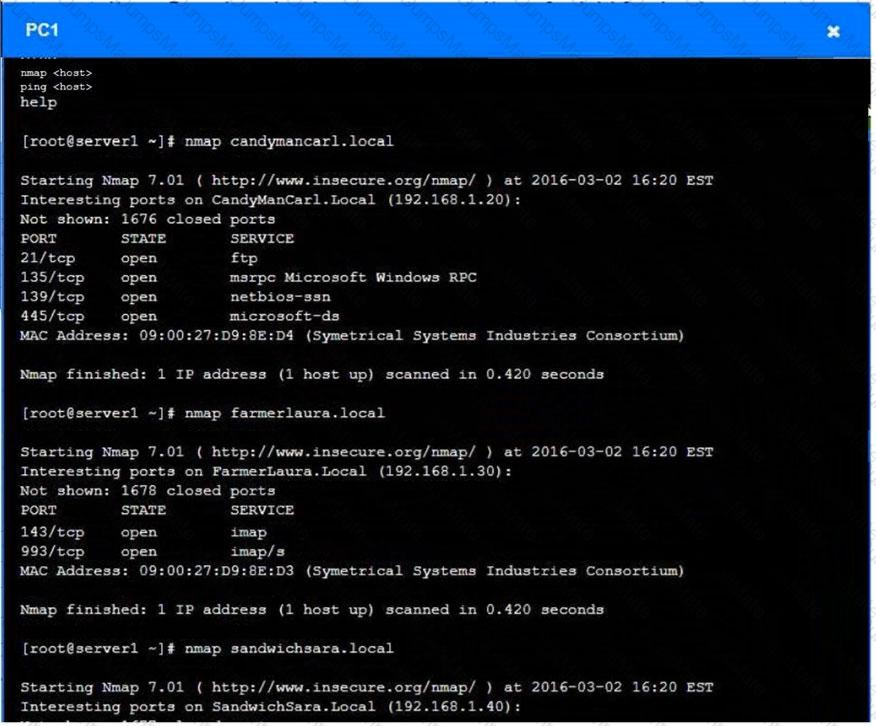
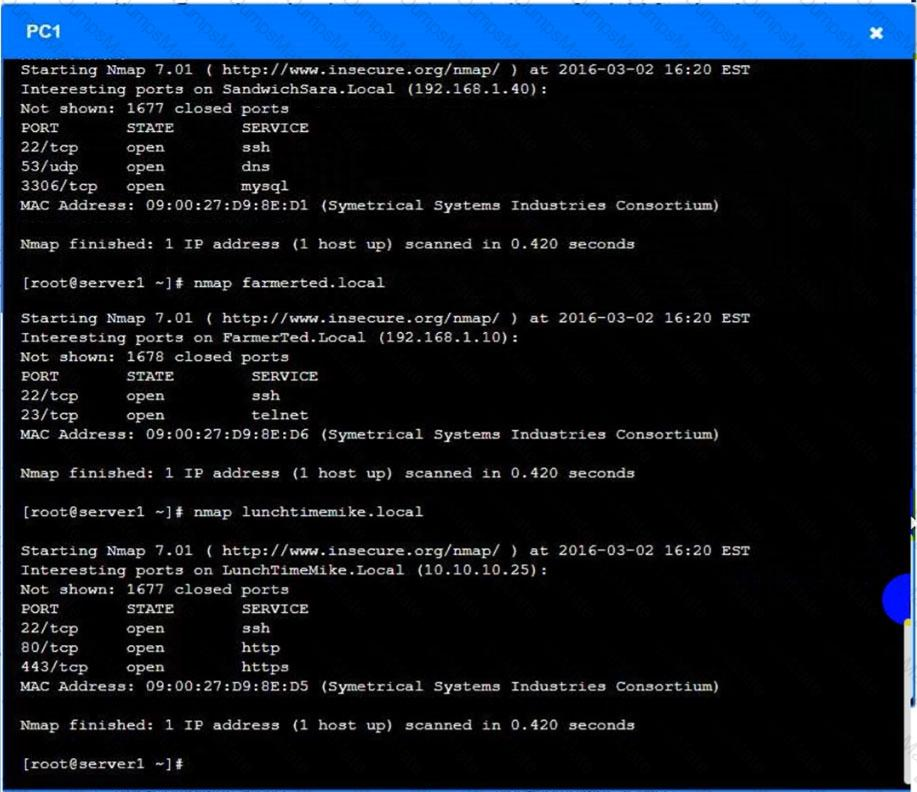
Question 10
After completing a review of network activity. the threat hunting team discovers a device on the network that sends an outbound email via a mail client to a non-company email address daily at 10:00 p.m. Which of the following is potentially occurring?
- Irregular peer-to-peer communication
- Rogue device on the network
- Abnormal OS process behavior
- Data exfiltration
Correct answer: D
Explanation:
Data exfiltration is the theft or unauthorized transfer or movement of data from a device or network. It can occur as part of an automated attack or manually, on-site or through an internet connection, and involve various methods. It can affect personal or corporate data, such as sensitive or confidential information. Data exfiltration can be prevented or detected by using compression, encryption, authentication, authorization, and other controls1The network activity shows that a device on the network is sending an outbound email via a mail client to a non-company email address daily at 10:00 p.m. This could indicate that the device is compromised by malware or an insider threat, and that the email is used to exfiltrate data from the network to an external party. The email could contain attachments, links, or hidden data that contain the stolen information. The timing of the email could be designed to avoid detection by normal network monitoring or security systems. Data exfiltration is the theft or unauthorized transfer or movement of data from a device or network. It can occur as part of an automated attack or manually, on-site or through an internet connection, and involve various methods. It can affect personal or corporate data, such as sensitive or confidential information. Data exfiltration can be prevented or detected by using compression, encryption, authentication, authorization, and other controls1
The network activity shows that a device on the network is sending an outbound email via a mail client to a non-company email address daily at 10:00 p.m. This could indicate that the device is compromised by malware or an insider threat, and that the email is used to exfiltrate data from the network to an external party.
The email could contain attachments, links, or hidden data that contain the stolen information. The timing of the email could be designed to avoid detection by normal network monitoring or security systems.
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



