Download CompTIA Cloud+.CV0-004.ExamTopics.2025-10-03.91q.vcex
| Vendor: | CompTIA |
| Exam Code: | CV0-004 |
| Exam Name: | CompTIA Cloud+ |
| Date: | Oct 03, 2025 |
| File Size: | 292 KB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
A software engineer needs to transfer data over the internet using programmatic access while also being able to query the data. Which of the following will best help the engineer to complete this task?
- SQL
- Web sockets
- RPC
- GraphQL
Correct answer: D
Explanation:
B: 2D: 1 - Mosted B: 2D: 1 - Mosted
Question 2
A company’s content management system (CMS) service runs on an IaaS cluster on a public cloud. The CMS service is frequently targeted by a malicious threat actor using DDoS.
Which of the following should a cloud engineer monitor to identify attacks?
- Network flow logs
- Endpoint detection and response logs
- Cloud provider event logs
- Instance syslog
Correct answer: A
Explanation:
A: 3B: 1 - Mosted A: 3B: 1 - Mosted
Question 3
Which of the following is the most cost-effective way to store data that is infrequently accessed?
- Cold site
- Hot site
- Off-site
- Warm site
Correct answer: C
Explanation:
C: 3 - Mosted C: 3 - Mosted
Question 4
Which of the following vulnerability management concepts is best defined as the process of discovering vulnerabilities?
- Scanning
- Assessment
- Remediation
- Identification
Correct answer: D
Explanation:
A: 2 - Mosted A: 2 - Mosted
Question 5
A company’s engineering department is conducting a month-long test on the scalability of an in-house-developed software that requires a cluster of 100 or more servers. Which of the following models is the best to use?
- PaaS
- SaaS
- DBaaS
- IaaS
Correct answer: A
Explanation:
A: 3 - Mosted A: 3 - Mosted
Question 6
Once a change has been made to templates, which of the following commands should a cloud architect use next to deploy an IaaS platform?
- git pull
- git fetch
- git commit
- git push
Correct answer: D
Explanation:
C: 1 C: 1
Question 7
A cloud networking engineer is troubleshooting the corporate office’s network configuration. Employees in the IT and operations departments are unable to resolve IP addresses on all devices, and the IT department cannot establish a connection to other departments’ subnets. The engineer identifies the following configuration currently in place to support the office network:
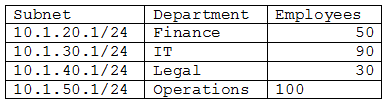
Each employee needs to connect to the network with a maximum of three hosts. Each subnet must be segregated, but the IT department must have the ability to communicate with all subnets. Which of the following meet the IP addressing and routing requirements? (Choose two.)
- Modifying the subnet mask to 255.255.254.0 for IT and operations departments
- Configuring static routing to allow access from each subnet to 10.1.40.1
- Modifying the BYOD policy to reduce the volume of devices that are allowed to connect to the corporate network
- Configuring static routing to allow access from 10.1.30.1 to each subnet
- Combining the subnets and increasing the allocation of IP addresses available to support three hosts for each employee
- Modifying the subnet mask to 255.255.255.128 for the IT and operations departments
Correct answer: AD
Explanation:
AD: 3 - Mosted AD: 3 - Mosted
Question 8
An organization’s critical data was exfiltrated from a computer system in a cyberattack. A cloud analyst wants to identify the root cause and is reviewing the following security logs of a software web application:
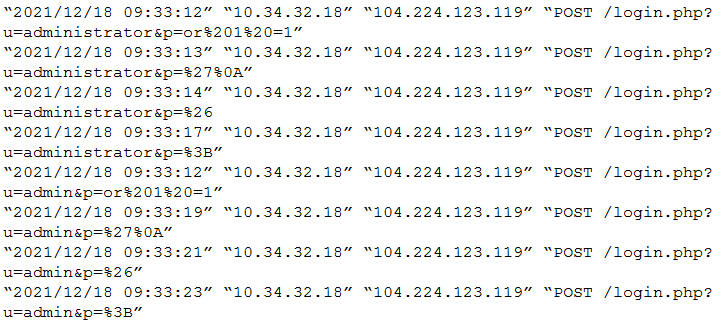
Which of the following types of attacks occurred?
- SQL injection
- Cross-site scripting
- Reuse of leaked credentials
- Privilege escalation
Correct answer: A
Explanation:
A: 1 A: 1
Question 9
Which of the following is a field of computer science that enables computers to identify and understand objects and people in images and videos?
- Image reconstruction
- Facial recognition
- Natural language processing
- Computer vision
Correct answer: D
Explanation:
D: 1 - Mosted D: 1 - Mosted
Question 10
A network administrator is building a site-to-site VPN tunnel from the company’s headquarters office to the company’s public cloud development network. The network administrator confirms the following:
- The VPN tunnel is established on the headquarters office firewall.
- While inside the office, developers report that they cannot connect to the development network resources.
- While outside the office on a client VPN, developers report that they can connect to the development network resources.
- The office and the client VPN have different IP subnet ranges.
- The firewall flow logs show that traffic is reaching the development network from the office.
Which of the following is the next step the network administrator should take to troubleshoot the VPN tunnel?
- Review the development network routing table.
- Change the ciphers on the site-to-site VPN.
- Restart the site-to-site VPN tunnel.
- Check the ACLs on the development workloads.
Correct answer: D
Explanation:
A: 1D: 3 - Mosted A: 1D: 3 - Mosted
Question 11
A developer sends multiple requests to a SaaS application in a short amount of time. The developer realizes that the entire server and all other users can no longer send requests to the application. Which of the following best describes the issue?
- Service quotas
- API rate limiting
- Full outage
- Regional service availability
Correct answer: B
Explanation:
C: 1 C: 1
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



