Download CyberArk Endpoint Privilege Manager.EPM-DEF.ExamTopics.2025-12-27.124q.tqb
| Vendor: | CyberArk |
| Exam Code: | EPM-DEF |
| Exam Name: | CyberArk Endpoint Privilege Manager |
| Date: | Dec 27, 2025 |
| File Size: | 1 MB |
How to open TQB files?
Files with TQB (Taurus Question Bank) extension can be opened by Taurus Exam Studio.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
What is the main reason to use the custom user access token for Elevate policies?
- to provide more privileges of permissions for the user
- to implement a less strict set of permissions for the user
- to provide least privileges of permissions for the user
- to impersonate the user with another set of permissions
Correct answer: D
Question 2
What is default retention period for admin activities on the web console?
- 14 days
- 30 days
- 90 days
- 1 year
Correct answer: B
Question 3
Refer to the exhibit.
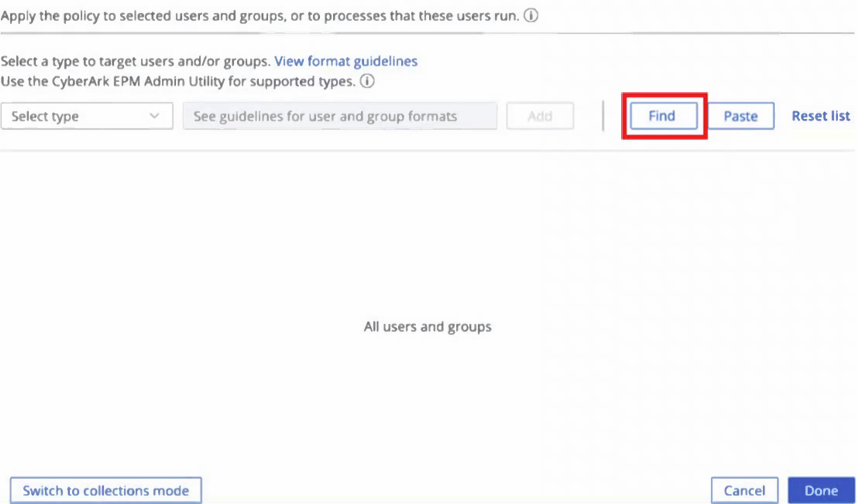
When editing an application policy, what does the "Find" button do?
- It opens all users and groups in EPM console
- It opens CyberArk Software to check if the connection with AD is working
- In the EPM admin utility, it opens a window to select users and group from AD or from the local endpoint
- In the EPM admin utility, it opens a page in the EPM console for you to select the users or group
Correct answer: C
Question 4
How many days after license expiration do EPM agents stop enforcing policies?
- 1
- 14
- 30
- 120
Correct answer: C
Question 5
When adding the EPM agent to a pre-existing security stack on workstation, what two steps are CyberArk recommendations. (Choose two.)
- Add any pre-existing security application to the Files to Be Ignored Always.
- Add EPM agent to the other security tools exclusions.
- EPM agent should never be run with any other security tools.
- Create new advanced policies for each security tool.
Correct answer: AB
Question 6
For the CyberArk EPM Threat Deception Credential Lure feature, what is the recommendation regarding the username creation?
- The username should match to an existing account.
- The username should have a strong password associated.
- The username should not match to an existing account.
- The username should match the built-in local Administrator.
Correct answer: C
Question 7
CyberArk EPM's Ransomware Protection comes with file types to be protected out of the box. If an EPM Administrator would like to remove a file type from Ransomware Protection, where can this be done?
- Policy Scope within Protect Against Ransomware
- Authorized Applications (Ransomware Protection) within Application Groups
- Set Security Permissions within Advanced Policies
- Protected Files within Agent Configurations
Correct answer: A
Question 8
When blocking applications, what is the recommended practice regarding the end-user UI?
- Show a block prompt for blocked applications.
- Show no prompts for blocked applications.
- Hide the CyberArk EPM Agent icon in the system tray.
- Enable the Default Deny policy.
Correct answer: A
Question 9
What is required to configure SAML authentication on EPM?
- OAuth token
- Signed Authentication Request
- Encrypted Assertion
- Signed SAML Response
Correct answer: B
Question 10
An EPM Administrator is looking to enable the Threat Deception feature, under what section should the EPM Administrator go to enable this feature?
- Threat Protection Inbox
- Policies
- Threat Intelligence
- Policy Audit
Correct answer: B
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



