Download Computer Hacking Forensic Investigator.312-49v10.ExamTopics.2025-11-29.197q.vcex
| Vendor: | ECCouncil |
| Exam Code: | 312-49v10 |
| Exam Name: | Computer Hacking Forensic Investigator |
| Date: | Nov 29, 2025 |
| File Size: | 750 KB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
You are contracted to work as a computer forensics investigator for a regional bank that has four 30 TB storage area networks that store customer data.
What method would be most efficient for you to acquire digital evidence from this network?
- create a compressed copy of the file with DoubleSpace
- create a sparse data copy of a folder or file
- make a bit-stream disk-to-image file
- make a bit-stream disk-to-disk file
Correct answer: C
Explanation:
C: 4 - Mosted C: 4 - Mosted
Question 2
After passively scanning the network of Department of Defense (DoD), you switch over to active scanning to identify live hosts on their network. DoD is a large organization and should respond to any number of scans. You start an ICMP ping sweep by sending an IP packet to the broadcast address. Only five hosts respond to your ICMP pings; definitely not the number of hosts you were expecting. Why did this ping sweep only produce a few responses?
- Only IBM AS/400 will reply to this scan
- Only Windows systems will reply to this scan
- A switched network will not respond to packets sent to the broadcast address
- Only Unix and Unix-like systems will reply to this scan
Correct answer: C
Explanation:
C: 7 - Mosted C: 7 - Mosted
Question 3
What is the slave device connected to the secondary IDE controller on a Linux OS referred to?
- hda
- hdd
- hdb
- hdc
Correct answer: B
Explanation:
B: 2C: 2 - Mosted B: 2C: 2 - Mosted
Question 4
What does 254 represent in ICCID 89254021520014515744?
- Industry Identifier Prefix
- Country Code
- Individual Account Identification Number
- Issuer Identifier Number
Correct answer: B
Explanation:
B: 1 - Mosted B: 1 - Mosted
Question 5
Which of the following file formats allows the user to compress the acquired data as well as keep it randomly accessible?
- Proprietary Format
- Generic Forensic Zip (gfzip)
- Advanced Forensic Framework 4
- Advanced Forensics Format (AFF)
Correct answer: D
Explanation:
B: 2D: 3 - Mosted B: 2D: 3 - Mosted
Question 6
Which layer of iOS architecture should a forensics investigator evaluate to analyze services such as Threading, File Access, Preferences, Networking and high- level features?
- Core Services
- Media services
- Cocoa Touch
- Core OS
Correct answer: A
Explanation:
A: 4 - MostedC: 1D: 3 A: 4 - MostedC: 1D: 3
Question 7
Which of the following is a non-zero data that an application allocates on a hard disk cluster in systems running on Windows OS?
- Sparse File
- Master File Table
- Meta Block Group
- Slack Space
Correct answer: A
Explanation:
A: 6 - Mosted A: 6 - Mosted
Question 8
You are a forensic investigator who is analyzing a hard drive that was recently collected as evidence. You have been unsuccessful at locating any meaningful evidence within the file system and suspect a drive wiping utility may have been used. You have reviewed the keys within the software hive of the Windows registry and did not find any drive wiping utilities. How can you verify that drive wiping software was used on the hard drive?
- Check the list of installed programs
- Look for distinct repeating patterns on the hard drive at the bit level
- Document in your report that you suspect a drive wiping utility was used, but no evidence was found
- Load various drive wiping utilities offline, and export previous run reports
Correct answer: B
Explanation:
B: 6 - Mosted B: 6 - Mosted
Question 9
What feature of Windows is the following command trying to utilize?
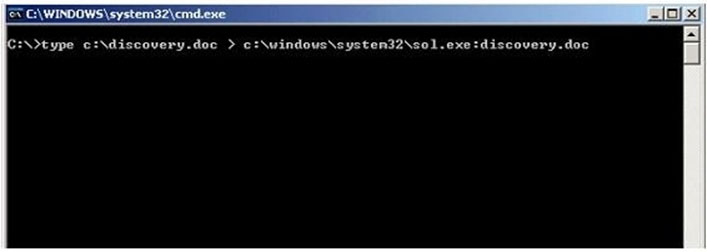
- White space
- AFS
- ADS
- Slack file
Correct answer: C
Question 10
Which legal document allows law enforcement to search an office, place of business, or other locale for evidence relating to an alleged crime?
- bench warrant
- wire tap
- subpoena
- search warrant
Correct answer: D
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



