Download Fortinet Network Security Expert 8 Written Exam.NSE8.ExamTopics.2025-09-25.24q.vcex
| Vendor: | Fortinet |
| Exam Code: | NSE8 |
| Exam Name: | Fortinet Network Security Expert 8 Written Exam |
| Date: | Sep 25, 2025 |
| File Size: | 7 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
The dashboard widget indicates that FortiGuard Web Filtering is not reachable. However, AntiVirus, IPS, and Application Control have no problems as shown in the exhibit.
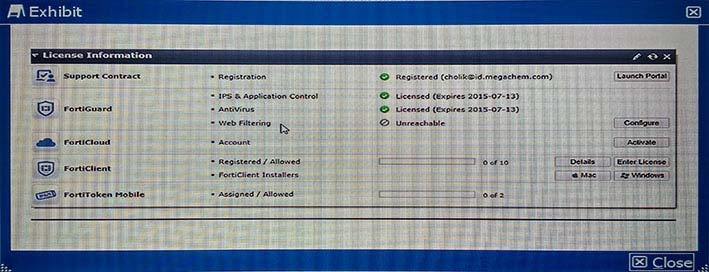
You contacted Fortinets customer service and discovered that your FortiGuard Web Filtering contract is still valid for several months.
What are two reasons for this problem? (Choose two.)
- You have another security device in front of FortiGate blocking ports 8888 and 53.
- FortiGuard Web Filtering is not enabled in any firewall policy.
- You did not enable Web Filtering cache under Web Filtering and E-mail Filtering Options.
- You have a firewall policy blocking ports 8888 and 53.
Correct answer: AB
Explanation:
If Web filtering shows unreachable then we have to verify, whether web filtering enabled in security policies or not.Web filtering enabled in a policy but the port 8888 and 53 are not selected, means the policy blocking the ports.Reference:http://cookbook.fortinet.com/troubleshooting-web-filtering/ If Web filtering shows unreachable then we have to verify, whether web filtering enabled in security policies or not.
Web filtering enabled in a policy but the port 8888 and 53 are not selected, means the policy blocking the ports.
Reference:
http://cookbook.fortinet.com/troubleshooting-web-filtering/
Question 2
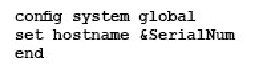
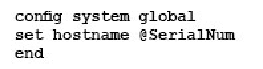
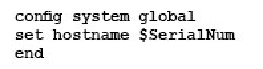
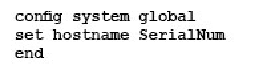
Which command syntax would you use to configure the serial number of a FortiGate as its host name?
Correct answer: C
Explanation:
http://docs.fortinet.com/uploaded/files/2002/FortiOS%20Handbook%20-%20System%20Administration%205.2.pdf http://docs.fortinet.com/uploaded/files/2002/FortiOS%20Handbook%20-%20System%20Administration%205.2.pdf
Question 3
A data center for example.com hosts several separate Web applications. Users authenticate with all of them by providing their Active Directory (AD) login credentials. You do not have access to Example, Inc.s AD server. Your solution must do the following:
- provide single sign-on (SSO) for all protected Web applications
- prevent login brute forcing
- scan FTPS connections to the Web servers for exploits
- scan Webmail for OWASP Top 10 vulnerabilities such as session cookie hijacking, XSS, and SQL injection attacks
Which solution meets these requirements?
- Apply FortiGate deep inspection to FTPS. It must forward FTPS, HTTP, and HTTPS to FortiWeb. Configure FortiWeb to query the AD server, and apply SSO for Web requests. FortiWeb must forward FTPS directly to the Web servers without inspection, but proxy HTTP/HTTPS and block Web attacks.
- Deploy FortiDDos to block brute force attacks. Configure FortiGate to forward only FTPS, HTTP, and HTTPS to FortiWeb. Configure FortiWeb to query the AD server, and apply SSO for Web requests. Also configure it to scan FTPS and Web traffic, then forward allowed traffic to the Web servers.
- Use FortiGate to authenticate and proxy HTTP/HTTPS; to verify credentials, FortiGate queries the AD server. Also configure FortiGate to scan FTPS before forwarding, and to mitigate SYN floods. Configure FortiWeb to block Web attacks.
- Install FSSO Agent on servers. Configure FortiGate to inspect FTPS. FortiGate will forward FTPS, HTTP, and HTTPS to FortiWeb. FortiWeb must block Web
Correct answer: D
Explanation:
A: 1 - MostedFSSO agent integrate fortigate with AD then inspect bruteforce,FTPS,HTTP, and HTTPS using fortiweb and then forward all traffic to web server.Reference:http://cookbook.fortinet.com/providing-single-sign-using-ldap-fsso-agent-advanced-mode-expert/ A: 1 - Mosted
FSSO agent integrate fortigate with AD then inspect bruteforce,FTPS,HTTP, and HTTPS using fortiweb and then forward all traffic to web server.
Reference:
http://cookbook.fortinet.com/providing-single-sign-using-ldap-fsso-agent-advanced-mode-expert/
Question 4
Which three configuration scenarios will result in an IPsec negotiation failure between two FortiGate devices? (Choose three.)
- mismatched phase 2 selectors
- mismatched Anti-Replay configuration
- mismatched Perfect Forward Secrecy
- failed Dead Peer Detection negotiation
- mismatched IKE version
Correct answer: ACE
Explanation:
ACE: 1In IPsec negotiations, Perfect Forward Secrecy (PFS) ensures that each new cryptographic key is unrelated to any previous key. Either enable or disable PFS on both the tunnel peers; otherwise, the LAN-to-LAN (L2L) IPsec tunnel is not established ACE: 1
In IPsec negotiations, Perfect Forward Secrecy (PFS) ensures that each new cryptographic key is unrelated to any previous key. Either enable or disable PFS on both the tunnel peers; otherwise, the LAN-to-LAN (L2L) IPsec tunnel is not established
Question 5
There is an interface-mode IPsec tunnel configured between FortiGate1 and FortiGate2. You want to run OSPF over the IPsec tunnel. On both FortiGates. the IPsec tunnel is based on physical interface port1. Port1 has the default MTU setting on both FortiGate units.
Which statement is true about this scenario?
- A multicast firewall policy must be added on FortiGate1 and FortiGate2 to allow protocol 89.
- The MTU must be set manually in the OSPF interface configuration.
- The MTU must be set manually on the IPsec interface.
- An IP address must be assigned to the IPsec interface on FortiGate1 and FortiGate2.
Correct answer: B
Explanation:
If MTU doesnt match then the neighbour ship gets stuck in exchange state. If MTU doesnt match then the neighbour ship gets stuck in exchange state.
Question 6
Which three statements about throughput on a wireless network are true? (Choose three.)
- A wireless device labelled as 300 Mbps should be expected to provide a throughput of 300Mbps.
- Be careful to ensure the capabilities of the wireless clients match those of the access points, in order to achieve higher throughput.
- Reducing the duty cycles of the wireless media by generating fewer beacons may improve throughput.
- Because of the higher level of RF noise that is typical in the 2.4 GHz ISM band, throughput of 2.4 GHz devices will typically be less than 5 GHz devices.
- Because of the full-duplex nature of the medium and the minimal overhead generated by CSMA/CA, the actual aggregate throughput is typically close to the
Correct answer: D
Explanation:
B: 1 - Mostedhttp://www.tp-link.in/faq-499.html B: 1 - Mosted
http://www.tp-link.in/faq-499.html
Question 7
An administrator wants to assign static IP addresses to users connecting tunnel-mode SSL VPN. Each SSL VPN user must always get the same unique IP address which is never assigned to any other user.
Which solution accomplishes this task?
- TACACS+ authentication with an attribute-value (AV) pair containing each user’s IP address.
- RADIUS authentication with each user’s IP address stored in a Vendor Specific Attribute (VSA).
- LDAP authentication with an LDAP attribute containing each user’s IP address.
- FSSO authentication with an LDAP attribute containing each user’s IP address.
Correct answer: D
Explanation:
B: 1 - Mosted B: 1 - Mosted
Question 8
You notice that memory usage is high and FortiGate has entered conserve mode. You want FortiGates IPS engine to focus only on exploits and attacks that are applicable to your specific network.
Which two steps would you take to reduce RAM usage without weakening security? (Choose two.)
- Configure IPS to pass files that are larger than a specific threshold, instead of buffering and scanning them.
- Reduce the size of the signature three (filters) that FortiGate must search by disabling scans for applications and OS stacks that do not exist on your network.
- Disable application control for protocols that are not used on your network.
- Disable IPS for traffic destined for the FortiGate itself.
Correct answer: AD
Explanation:
BC: 1 - Mosted BC: 1 - Mosted
Question 9
You verified that application control is working from previous configured categories. You just added Skype on blocked signatures. However, after applying the profile to your firewall policy, clients running Skype can still connect and use the application.
What are two causes of this problem? (Choose two.)
- The application control database is not updated.
- SSL inspection is not enabled.
- A client on the network was already connected to the Skype network and serves as relay prior to configuration changes to block Skype
- The FakeSkype.botnet signature is included on your application control sensor.
Correct answer: AB
Question 10
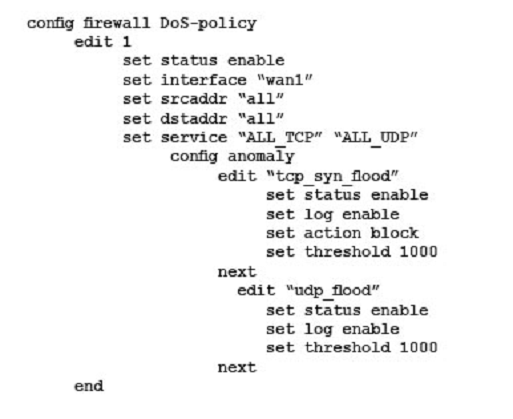
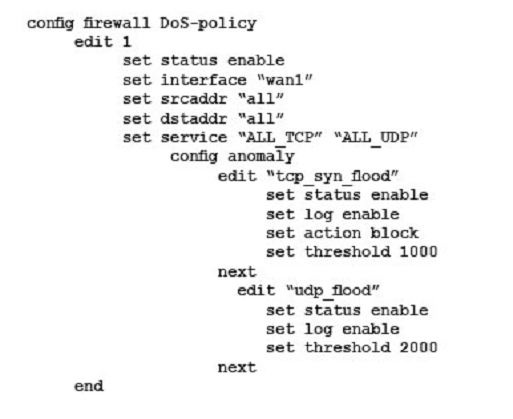
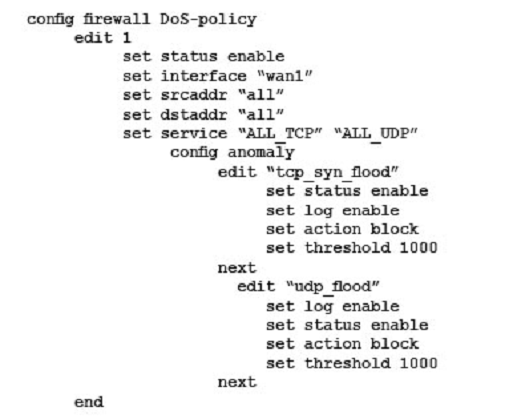
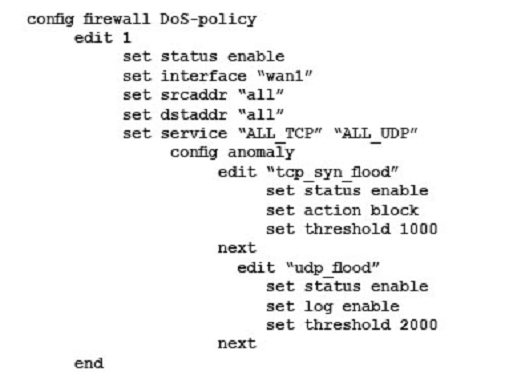
A company wants to protect against Denial of Service attacks and has launched a new project. They want to block the attacks that go above a certain threshold and for some others they are just trying to get a baseline of activity for those types of attacks so they are letting the traffic pass through without action. Given the following:
- The interface to the Internet is on WAN1.
- There is no requirement to specify which addresses are being protected or protected from.
- The protection is to extend to all services.
- The tcp_syn_flood attacks are to be recorded and blocked.
- The udp_flood attacks are to be recorded but not blocked.
- The tcp_syn_flood attacks threshold is to be changed from the default to 1000.
The exhibit shows the current DoS-policy.
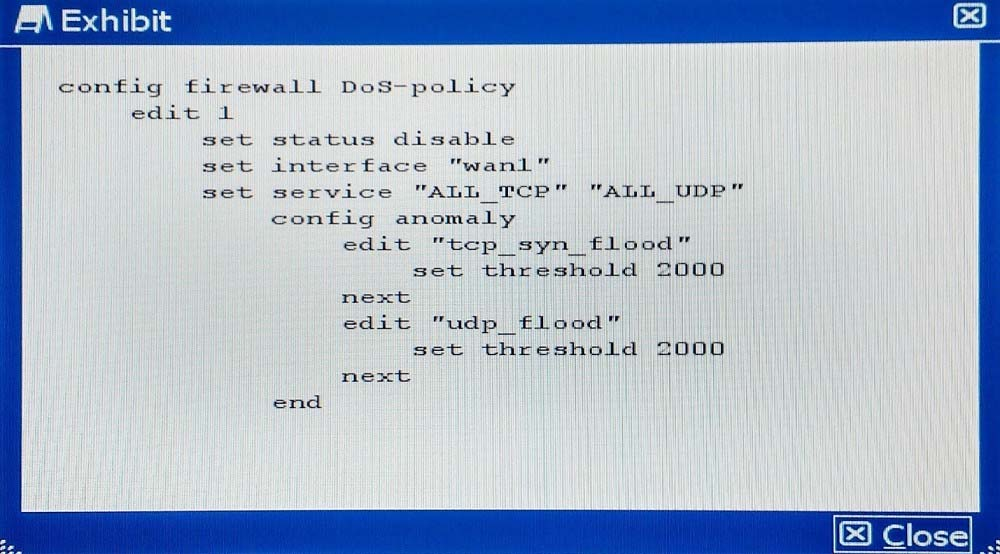
Which policy will implement the project requirements?
Correct answer: BD
Explanation:
B&D both have same policy which fulfills the above criteria.http://help.fortinet.com/fos50hlp/52data/Content/FortiOS/fortigate-firewall-52/Examples/Example-%20DoS%20Policy.htm B&D both have same policy which fulfills the above criteria.
http://help.fortinet.com/fos50hlp/52data/Content/FortiOS/fortigate-firewall-52/Examples/Example-%20DoS%20Policy.htm
Question 11
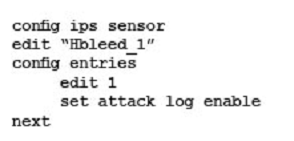
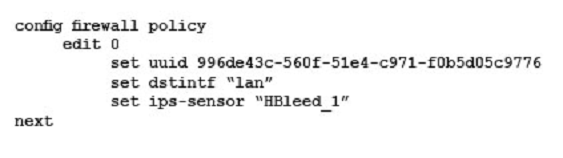
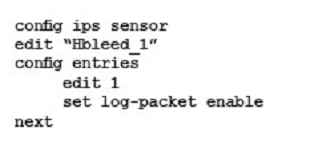
Your security department has requested that you implement the OpenSSL.TLS.Heartbeat.Information.Disclosure signature using an IPS sensor to scan traffic destined to the FortiGate. You must log all packets that attempt to exploit this vulnerability.
Referring to the exhibit, which two configurations are required to accomplish this task? (Choose two.)
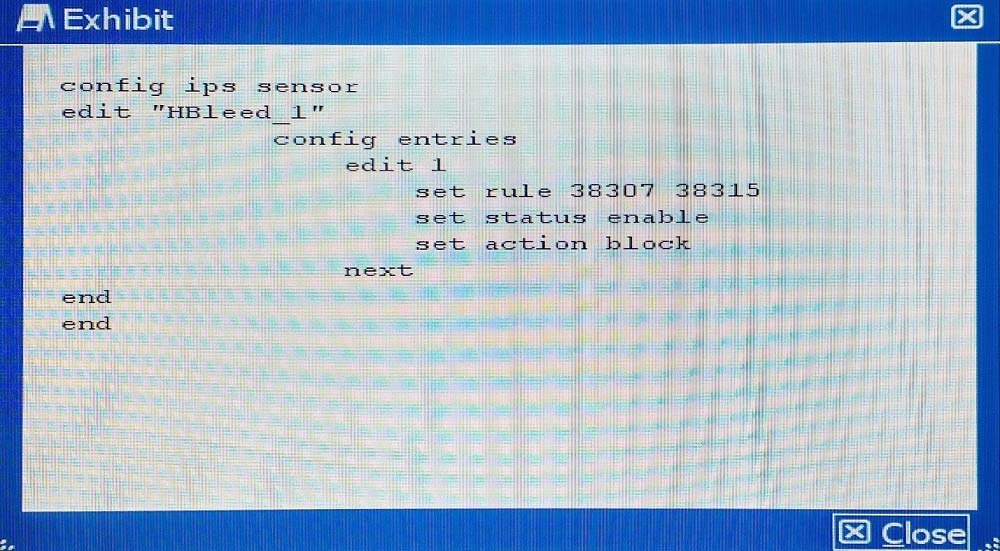
Correct answer: AB
Explanation:
AD: 1 - Mostedhttp://defadhil.blogspot.in/2014/04/how-to-protect-fortigate-from.html AD: 1 - Mosted
http://defadhil.blogspot.in/2014/04/how-to-protect-fortigate-from.html
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!