Download Microsoft Azure Security Technologies.AZ-500.ExamTopics.2026-01-21.437q.vcex
| Vendor: | Microsoft |
| Exam Code: | AZ-500 |
| Exam Name: | Microsoft Azure Security Technologies |
| Date: | Jan 21, 2026 |
| File Size: | 32 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
What is the membership of Group1 and Group2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
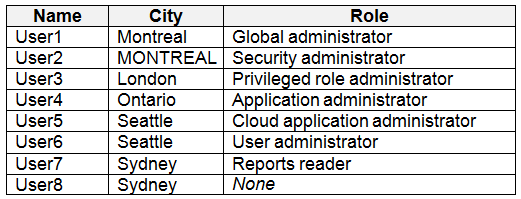
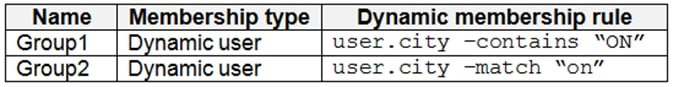
Box 1: User1, User2, User3, User4Contains "ON" is true for Montreal (User1), MONTREAL (User2), London (User 3), and Ontario (User4) as string and regex operations are not case sensitive.Box 2: Only User3 -Match "*on" is only true for London (User3) as 'London' is the only word that ends with 'on'.Scenario:Contoso.com contains the users shown in the following table. Contoso.com contains the security groups shown in the following table. References:https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-dynamic-membership Box 1: User1, User2, User3, User4
Contains "ON" is true for Montreal (User1), MONTREAL (User2), London (User 3), and Ontario (User4) as string and regex operations are not case sensitive.
Box 2: Only User3 -
Match "*on" is only true for London (User3) as 'London' is the only word that ends with 'on'.
Scenario:
Contoso.com contains the users shown in the following table.
Contoso.com contains the security groups shown in the following table.
References:
https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-dynamic-membership
Question 2
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription named Sub1.
You have an Azure Storage account named sa1 in a resource group named RG1.
Users and applications access the blob service and the file service in sa1 by using several shared access signatures (SASs) and stored access policies.
You discover that unauthorized users accessed both the file service and the blob service.
You need to revoke all access to sa1.
Solution: You generate new SASs.
Does this meet the goal?
- Yes
- No
Correct answer: B
Explanation:
B: 8 - Mosted B: 8 - Mosted
Question 3
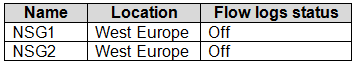
You have an Azure subscription that contains a resource group named RG1 and the network security groups (NSGs) shown in the following table.
You create and assign the Azure policy shown in the following exhibit.
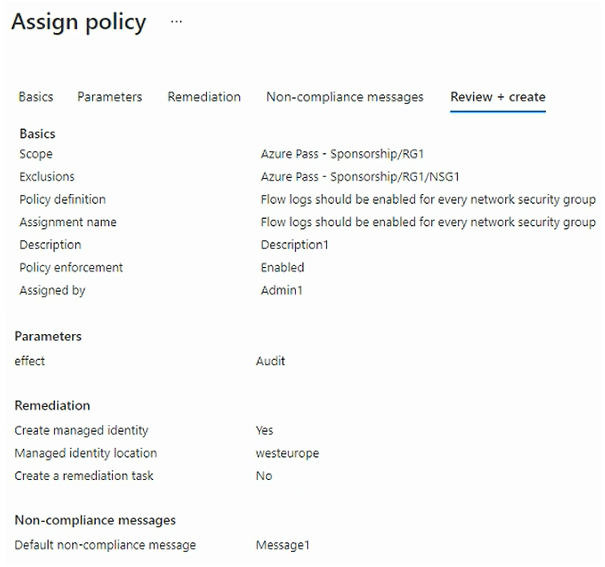
What is the flow log status of NSG1 and NSG2 after the Azure policy is assigned?
- Flow logs will be enabled for NSG1 only.
- Flow logs will be enabled for NSG2 only.
- Flow logs will be enabled for NSG1 and NSG2.
- Flow logs will be disabled for NSG1 and NSG2.
Correct answer: D
Explanation:
D: 21 - Mosted D: 21 - Mosted
Question 4
Your on-premises network contains a Hyper-V virtual machine named VM1.
You need to use Azure Arc to onboard VM1 to Microsoft Defender for Cloud.
What should you install first?
- the guest configuration agent
- the Azure Monitor agent
- the Log Analytics agent
- the Azure Connected Machine agent
Correct answer: D
Explanation:
C: 4D: 27 - Mosted C: 4D: 27 - Mosted
Question 5
You have an Azure subscription that contains a Microsoft Defender External Attack Surface Management (Defender EASM) resource named EASM1. EASM1 has discovery enabled and contains several inventory assets.
You need to identify which inventory assets are vulnerable to the most critical web app security risks.
Which Defender EASM dashboard should you use?
- Security Posture
- OWASP Top 10
- Attack Surface Summary
- GDPR Compliance
Correct answer: B
Explanation:
B: 13 - Mosted B: 13 - Mosted
Question 6
You have an Azure subscription that uses Microsoft Defender for Cloud.
You need to use Defender for Cloud to review regulatory compliance with the Azure CIS 1.4.0 standard. The solution must minimize administrative effort.
What should you do first?
- Assign an Azure policy.
- Disable one of the Out of the box standards.
- Manually add the Azure CIS 1.4.0 standard.
- Add a custom initiative.
Correct answer: C
Explanation:
A: 4C: 20 - Mosted A: 4C: 20 - Mosted
Question 7
You have an Azure subscription that contains an Azure key vault named Vault1 and a virtual machine named VM1.
VM1 is connected to a virtual network named VNet1.
You need to allow access to Vault1 only from VM1.
What should you do in the Networking settings of Vault1?
- From the Firewalls and virtual networks tab, add the IP address of VM1.
- From the Private endpoint connections tab, create a private endpoint for VM1.
- From the Firewalls and virtual networks tab, add VNet1.
- From the Firewalls and virtual networks tab, set Allow trusted Microsoft services to bypass this firewall to Yes for Vault1.
Correct answer: A
Explanation:
A: 25 - MostedB: 6C: 7 A: 25 - MostedB: 6C: 7
Question 8
You have an Azure subscription.
You create a new virtual network named VNet1.
You plan to deploy an Azure web app named App1 that will use VNet1 and will be reachable by using private IP addresses.
The solution must support inbound and outbound network traffic.
What should you do?
- Create an Azure App Service Hybrid Connection.
- Create an Azure application gateway.
- Create an App Service Environment.
- Configure regional virtual network integration.
Correct answer: C
Explanation:
C: 16 - MostedD: 3 C: 16 - MostedD: 3
Question 9
You have an Azure subscription that contains a user named User1.
You need to ensure that User1 can perform the following tasks:
- Create groups.
- Create access reviews for role-assignable groups.
- Assign Azure AD roles to groups.
The solution must use the principle of least privilege.
Which role should you assign to User1?
- Groups administrator
- Authentication administrator
- Identity Governance Administrator
- Privileged role administrator
Correct answer: D
Explanation:
A: 1C: 2D: 15 - Mosted A: 1C: 2D: 15 - Mosted
Question 10
You have an Azure subscription that contains a storage account named storage1 and a virtual machine named VM1.
VM1 is connected to a virtual network named VNet1 that contains one subnet and uses Azure DNS.
You need to ensure that VM1 connects to storage1 by using a private IP address. The solution must minimize administrative effort.
What should you do?
- For storage1, disable public network access.
- On VNet1, create a new subnet.
- For storage1, create a new private endpoint.
- Create an Azure Private DNS zone.
Correct answer: C
Explanation:
C: 12 - Mosted C: 12 - Mosted
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



