Download Microsoft Security Operations Analyst.SC-200.ExamTopics.2026-01-03.93q.vcex
| Vendor: | Microsoft |
| Exam Code: | SC-200 |
| Exam Name: | Microsoft Security Operations Analyst |
| Date: | Jan 03, 2026 |
| File Size: | 4 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
You have a Microsoft 365 E5 subscription that uses Microsoft 365 Defender.
You need to review new attack techniques discovered by Microsoft and identify vulnerable resources in the subscription. The solution must minimize administrative effort.
Which blade should you use in the Microsoft 365 Defender portal?
- Advanced hunting
- Threat analytics
- Incidents & alerts
- Learning hub
Correct answer: B
Explanation:
B: 8 - Mosted B: 8 - Mosted
Question 2
You have an Azure subscription that uses Microsoft Defender for Cloud.
You create a Google Cloud Platform (GCP) organization named GCP1.
You need to onboard GCP1 to Defender for Cloud by using the native cloud connector. The solution must ensure that all future GCP projects are onboarded automatically.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Question 3
You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365.
You need to ensure that you can investigate threats by using data in the unified audit log of Microsoft Defender for Cloud Apps.
What should you configure first?
- the User enrichment settings
- the Azure connector
- the Office 365 connector
- the Automatic log upload settings
Correct answer: C
Explanation:
C: 15 - Mosted C: 15 - Mosted
Question 4
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint.
You need to identify any devices that triggered a malware alert and collect evidence related to the alert. The solution must ensure that you can use the results to initiate device isolation for the affected devices.
What should you use in the Microsoft 365 Defender portal?
- incidents
- Remediation
- Investigations
- Advanced hunting
Correct answer: D
Explanation:
A: 11C: 3D: 26 - Mosted A: 11C: 3D: 26 - Mosted
Question 5
You have an Azure subscription that uses Microsoft Sentinel and contains a user named User1.
You need to ensure that User1 can enable User and Entity Behavior Analytics (UEBA) for entity behavior in Azure AD. The solution must use the principle of least privilege.
Which roles should you assign to User1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Question 6
You have an Azure subscription that contains the following resources:
- A virtual machine named VM1 that runs Windows Server
- A Microsoft Sentinel workspace named Sentinel1 that has User and Entity Behavior Analytics (UEBA) enabled
You have a scheduled query rule named Rule1 that tracks sign-in attempts to VM1.
You need to update Rule1 to detect when a user from outside the IT department of your company signs in to VM1. The solution must meet the following requirements:
- Utilize UEBA results.
- Maximize query performance.
- Minimize the number of false positives.
How should you complete the rule definition? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Question 7
You have a Microsoft 365 E5 subscription that contains 100 Linux devices. The devices are onboarded to Microsoft Defender 365.
You need to initiate the collection of investigation packages from the devices by using the Microsoft 365 Defender portal.
Which response action should you use?
- Run antivirus scan
- Initiate Automated Investigation
- Collect investigation package
- Initiate Live Response Session
Correct answer: C
Explanation:
C: 10 - MostedD: 5 C: 10 - MostedD: 5
Question 8
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
Litware Inc. is a renewable energy company.
Litware has offices in Boston and Seattle. Litware also has remote users located across the United States. To access Litware resources, including cloud resources, the remote users establish a VPN connection to either office.
Existing Environment
Identity Environment
The network contains an Active Directory forest named litware.com that syncs to an Azure Active Directory (Azure AD) tenant named litware.com.
Microsoft 365 Environment
Litware has a Microsoft 365 E5 subscription linked to the litware.com Azure AD tenant. Microsoft Defender for Endpoint is deployed to all computers that run Windows 10. All Microsoft Defender for Cloud Apps built-in anomaly detection policies are enabled.
Azure Environment
Litware has an Azure subscription linked to the litware.com Azure AD tenant. The subscription contains resources in the East US Azure region as shown in the following table.

Network Environment
Each Litware office connects directly to the internet and has a site-to-site VPN connection to the virtual networks in the Azure subscription.
On-premises Environment
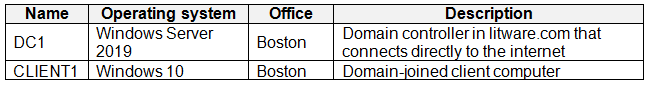
The on-premises network contains the computers shown in the following table.
Current Problems
Microsoft Defender for Cloud Apps frequently generates false positive alerts when users connect to both offices simultaneously.
Planned Changes and Requirements
Planned Changes
Litware plans to implement the following changes:
- Create and configure Microsoft Sentinel in the Azure subscription.
- Validate Microsoft Sentinel functionality by using Azure AD test user accounts.
Business Requirements
Litware identifies the following business requirements:
- The principle of least privilege must be used whenever possible.
- Costs must be minimized, as long as all other requirements are met.
- Logs collected by Log Analytics must provide a full audit trail of user activities.
- All domain controllers must be protected by using Microsoft Defender for Identity.
Azure Information Protection Requirements
All files that have sensitivity labels and are stored on the Windows 10 computers must be available from the Azure Information Protection – Data discovery dashboard.
Microsoft Defender for Endpoint Requirements
All Microsoft Defender for Cloud Apps unsanctioned apps must be blocked on the Windows 10 computers by using Microsoft Defender for Endpoint.
Microsoft Defender for Cloud Apps Security Requirements
Microsoft Defender for Cloud Apps must identify whether a user connection is anomalous based on tenant-level data.
Microsoft Defender for Cloud Requirements
All servers must send logs to the same Log Analytics workspace.
Microsoft Sentinel Requirements
Litware must meet the following Microsoft Sentinel requirements:
- Integrate Microsoft Sentinel and Microsoft Defender for Cloud Apps.
- Ensure that a user named admin1 can configure Microsoft Sentinel playbooks.
- Create a Microsoft Sentinel analytics rule based on a custom query. The rule must automatically initiate the execution of a playbook.
- Add notes to events that represent data access from a specific IP address to provide the ability to reference the IP address when navigating through an investigation graph while hunting.
- Create a test rule that generates alerts when inbound access to Microsoft Office 365 by the Azure AD test user accounts is detected. Alerts generated by the rule must be grouped into individual incidents, with one incident per test user account.
You need to configure DC1 to meet the business requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Correct answer: To work with this question, an Exam Simulator is required.
Question 9
You have a Microsoft 365 subscription that uses Microsoft Purview and Microsoft Teams.
You have a team named Team1 that has a project named Project1.
You need to identify any Project1 files that were stored on the team site of Team1 between February 1, 2023, and February 10, 2023.
Which KQL query should you run?
- (c:c)(Project1)(date=(2023-02-01)..date=(2023-02-10))
- AuditLogs -| where Timestamp between (datetime(2023-02-01)..datetime(2023-02-10))| where FileName contains “Project1”
- Project1(c:c)(date=2023-02-01..2023-02-10)
- AuditLogs -| where Timestamp > ago(10d)| where FileName contains “Project1”
Correct answer: C
Explanation:
B: 7C: 12 - Mosted B: 7C: 12 - Mosted
Question 10
You have a Microsoft 365 E5 subscription that uses Microsoft Teams.
You need to perform a content search of Teams chats for a user by using the Microsoft Purview compliance portal. The solution must minimize the scope of the search.
How should you configure the content search? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



