Download NetApp Certified Implementation Engineer - Data Protection.NS0-528.Braindump2go.2025-11-06.33q.vcex
| Vendor: | NetApp |
| Exam Code: | NS0-528 |
| Exam Name: | NetApp Certified Implementation Engineer - Data Protection |
| Date: | Nov 06, 2025 |
| File Size: | 85 KB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
An administrator is setting up SnapMirror SVM replication. One of the source data volumes uses cloud tiering with the snapshot-only tiering policy.
Which cloud tiering policy is supported on the destination volume?
- none
- auto
- all
- snapshot-only
Correct answer: D
Explanation:
When using SnapMirror SVM replication, the cloud tiering policy on the destination volume must match the source if tiering is to be preserved. The only supported tiering policy in this context is snapshot-only, which moves cold Snapshot blocks to cloud tier. This ensures compatibility during replication. When using SnapMirror SVM replication, the cloud tiering policy on the destination volume must match the source if tiering is to be preserved. The only supported tiering policy in this context is snapshot-only, which moves cold Snapshot blocks to cloud tier. This ensures compatibility during replication.
Question 2
What are the two modes for Autonomous Ransomware Protection (ARP)? (Choose two.)
- active
- listening
- passive
- learning
Correct answer: AD
Explanation:
Autonomous Ransomware Protection (ARP) operates in two modes:Learning mode: ARP observes and learns baseline workload behaviors to distinguish between normal and abnormal activity.Active mode: ARP actively monitors and can automatically respond to ransomware-like behavior by alerting or taking protective actions. Autonomous Ransomware Protection (ARP) operates in two modes:
Learning mode: ARP observes and learns baseline workload behaviors to distinguish between normal and abnormal activity.
Active mode: ARP actively monitors and can automatically respond to ransomware-like behavior by alerting or taking protective actions.
Question 3
You have created a SnapMirror relationship from your production volume serving SMB/CIFS data to your DR cluster. After two days of updates, you do not see any of the expected snapshots on the secondary volume.
Why is SnapMirror failing to replicate snapshots?
- The SnapMirror label is missing from the SnapMirror policy on the secondary volume.
- SnapMirror is not properly licensed.
- SVM peering is not properly configured.
- The SnapMirror label is missing from the snapshot policy on the secondary volume.
Correct answer: D
Explanation:
SnapMirror replication is driven by labels that match between the snapshot policy on the source volume and the SnapMirror policy. If the snapshot policy on the source does not include the correct SnapMirror label, SnapMirror will not recognize which snapshots to replicate, resulting in no transfers. SnapMirror replication is driven by labels that match between the snapshot policy on the source volume and the SnapMirror policy. If the snapshot policy on the source does not include the correct SnapMirror label, SnapMirror will not recognize which snapshots to replicate, resulting in no transfers.
Question 4
Which native NetApp ONTAP solution protects data by using machine learning to identify abnormal activity?
- Cloud Insights
- Autonomous Ransomware Protection
- external FPolicy engine
- internal FPolicy engine
Correct answer: B
Explanation:
Autonomous Ransomware Protection (ARP) is a native NetApp ONTAP feature that uses machine learning to monitor and analyze file activity patterns. It detects anomalies such as sudden spikes in file changes — typical of ransomware behavior — and automatically alerts or blocks access to limit potential damage. Autonomous Ransomware Protection (ARP) is a native NetApp ONTAP feature that uses machine learning to monitor and analyze file activity patterns. It detects anomalies such as sudden spikes in file changes — typical of ransomware behavior — and automatically alerts or blocks access to limit potential damage.
Question 5
You have a requirement to keep multiple yearly Snapshot copies on your SnapMirror destination volume. However, you do not want to have the Snapshot copies locked on your source volume because you do not have the required capacity.
Where do you set the schedule option to create the required Snapshot copies?
- primary SnapMirror policy
- secondary Snapshot policy
- primary Snapshot policy
- secondary SnapMirror policy
Correct answer: B
Explanation:
To retain multiple yearly Snapshot copies only on the SnapMirror destination, you must apply a Snapshot policy on the secondary volume. This avoids consuming space on the source volume, as these Snapshots are created and retained independently on the destination. To retain multiple yearly Snapshot copies only on the SnapMirror destination, you must apply a Snapshot policy on the secondary volume. This avoids consuming space on the source volume, as these Snapshots are created and retained independently on the destination.
Question 6
What two types of Compliance Clocks are available on NetApp ONTAP software? (Choose two.)
- volume
- SVM
- NTP
- system
Correct answer: AD
Explanation:
NetApp ONTAP supports two types of Compliance Clocks for write once, read many (WORM) and SnapLock compliance:The system Compliance Clock is maintained at the cluster level and ensures tamperproof retention.The volume Compliance Clock is specific to SnapLock volumes and is used to enforce retention periods at the volume level. NetApp ONTAP supports two types of Compliance Clocks for write once, read many (WORM) and SnapLock compliance:
The system Compliance Clock is maintained at the cluster level and ensures tamperproof retention.
The volume Compliance Clock is specific to SnapLock volumes and is used to enforce retention periods at the volume level.
Question 7
A ransomware attack has compromised all files on a CIFS share. The volume had a retention policy of five daily Snapshot copies, but unfortunately, no Snapshot copies were available. It was confirmed that the cybercriminal accessed only the share and did not gain access to the NetApp ONTAP cluster.
What command should be executed to prevent the quick restore strategy from being compromised?
- volume autosize -autogrow disable
- security multi-admin-verify modify -enabled true
- volume modify -snapdir-access false
- volume snapshot -autodelete disabled
Correct answer: C
Explanation:
Setting snapdir-access to false prevents users accessing the CIFS/NFS share from viewing or deleting Snapshot copies via the .snapshot directory. This secures the Snapshot restore mechanism from being exposed or tampered with in case of another attack through file shares. Setting snapdir-access to false prevents users accessing the CIFS/NFS share from viewing or deleting Snapshot copies via the .snapshot directory. This secures the Snapshot restore mechanism from being exposed or tampered with in case of another attack through file shares.
Question 8
Your customer wants to use tamper-proof Snapshot copies on a SnapMirror destination volume only.
You successfully created a SnapMirror relationship using a SnapMirror policy that contains the following rules:
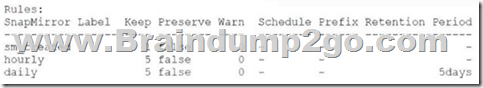
After initializing, you are able to delete a daily Snapshot copy.
Which command did you need to modify to enable the tamper-proof Snapshot copies as specified in the policy?
- volume modify -snapshot-locking-enabled
- volume snaplock modify -privileged-delete
- vserver modify -snapshot-policy
- volume snapshot modify -expiry-time
Correct answer: A
Explanation:
Although the SnapMirror policy includes rules for retaining Snapshot copies, the ability to make them tamper-proof (i.e., locked) depends on enabling snapshot locking on the destination volume. You must explicitly run:volume modify -volume -snapshot-locking-enabled trueWithout this setting, SnapMirror-created Snapshot copies can still be deleted manually. Enabling snapshot-locking ensures that retention rules (like the 5-day daily rule in your policy) are enforced and Snapshots are immutable. Although the SnapMirror policy includes rules for retaining Snapshot copies, the ability to make them tamper-proof (i.e., locked) depends on enabling snapshot locking on the destination volume. You must explicitly run:
volume modify -volume -snapshot-locking-enabled true
Without this setting, SnapMirror-created Snapshot copies can still be deleted manually. Enabling snapshot-locking ensures that retention rules (like the 5-day daily rule in your policy) are enforced and Snapshots are immutable.
Question 9
You have three clusters and want to set up a data protection relationship between Cluster1 and Cluster2 and also between Cluster1 and Cluster3. You want to make sure that the traffic between these two relationships is separated.
What must be configured on Clusterl to enable cluster peering with the other two clusters?
- broadcast domains
- IPspaces
- VLANs
- interface groups
Correct answer: B
Explanation:
To separate traffic for different cluster peering relationships on the same cluster (Cluster1), you need to configure IPspaces. IPspaces allow multiple logical network domains within a single ONTAP cluster, ensuring that peering traffic to Cluster2 and Cluster3 remains isolated. To separate traffic for different cluster peering relationships on the same cluster (Cluster1), you need to configure IPspaces. IPspaces allow multiple logical network domains within a single ONTAP cluster, ensuring that peering traffic to Cluster2 and Cluster3 remains isolated.
Question 10
You are setting up replication between a primary site that has a six-node NetApp cluster and a secondary site that has a two-node NetApp cluster.
What is the minimum number of required Intercluster LIFs?
- The primary site requires one, and the secondary site requires one.
- The primary site requires six, and the secondary site requires two.
- The primary site requires two, and the secondary site requires two.
- The primary site requires twelve, and the secondary site requires four.
Correct answer: B
Explanation:
Each node in a NetApp cluster must have at least one Intercluster LIF to participate in SnapMirror replication. Therefore, for a six-node cluster (primary), you need six LIFs, and for a two-node cluster (secondary), you need two LIFs — one per node. Each node in a NetApp cluster must have at least one Intercluster LIF to participate in SnapMirror replication. Therefore, for a six-node cluster (primary), you need six LIFs, and for a two-node cluster (secondary), you need two LIFs — one per node.
Question 11
You are using NetApp SnapCenter software to back up several Oracle, SQL, and Exchange instances.
What needs to be created in order to verify application consistency for each application within SnapCenter?
- a resource group that includes all volumes
- a consistency group for each application that includes the correct resource groups
- a resource group for each application that includes the correct consistency groups
- a consistency group that includes all volumes
Correct answer: B
Explanation:
In SnapCenter, to ensure application-consistent backups for Oracle, SQL, and Exchange, you must create a consistency group for each application. These groups organize the correct resource groups (which define the backup scope) and ensure all related components are captured in a consistent state during the backup. In SnapCenter, to ensure application-consistent backups for Oracle, SQL, and Exchange, you must create a consistency group for each application. These groups organize the correct resource groups (which define the backup scope) and ensure all related components are captured in a consistent state during the backup.
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



