Download Netskope Certified Cloud Security Integrator.NSK300.ExamTopics.2025-10-08.36q.tqb
| Vendor: | Netskope |
| Exam Code: | NSK300 |
| Exam Name: | Netskope Certified Cloud Security Integrator |
| Date: | Oct 08, 2025 |
| File Size: | 909 KB |
How to open TQB files?
Files with TQB (Taurus Question Bank) extension can be opened by Taurus Exam Studio.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
Review the exhibit.
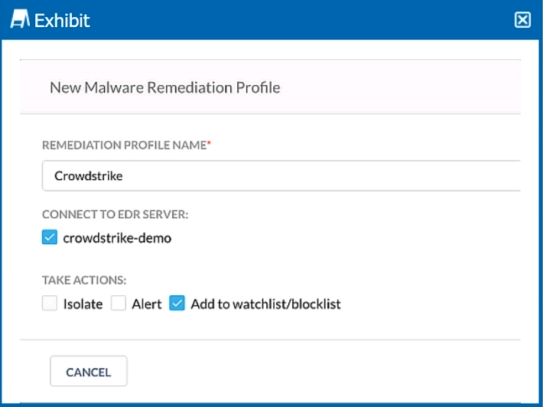
You are asked to integrate Netskope with Crowdstrike EDR. You added the Remediation profile shown in the exhibit.
Which action will this remediation profile take?
- The endpoint will be isolated.
- The malware hash will be added as an IOC in Crowdstrike.
- The malware will be quarantined.
- The malware hash will be added as an IOC in Netskope.
Correct answer: A
Explanation:
B: 2 B: 2
Question 2
You are building an architecture plan to roll out Netskope for on-premises devices. You determine that tunnels are the best way to achieve this task due to a lack of support for explicit proxy in some instances and IPsec is the right type of tunnel to achieve the desired security and steering.
What are three valid elements that you must consider when using IPsec tunnels in this scenario? (Choose three.)
- cipher support on tunnel-initiating devices
- bandwidth considerations
- the categories to be blocked
- the impact of threat scanning performance
- Netskope Client behavior when on-premises
Correct answer: ABD
Explanation:
ABE: 2 ABE: 2
Question 3
You are asked to create a customized restricted administrator role in your Netskope tenant for a newly hired employee.
Which two statements are correct in this scenario? (Choose two.)
- An admin role prevents admins from downloading and viewing file content by default.
- The scope of the data shown in the UI can be restricted to specific events.
- All role privileges default to Read Only for all functional areas.
- Obfuscation can be applied to all functional areas.
Correct answer: BC
Explanation:
BD: 2 BD: 2
Question 4
You are architecting a Netskope steering configuration for devices that are not owned by the organization. The users could be either on-premises or off-premises and the architecture requires that traffic destined to the company’s instance of Microsoft 365 be steered to Netskope for inspection.
How would you achieve this scenario from a steering perspective?
- Use IPsec and GRE tunnels.
- Use reverse proxy.
- Use explicit proxy and the Netskope Client.
- Use DPoP and Secure Forwarder.
Correct answer: C
Explanation:
B: 1 B: 1
Question 5
You are using Netskope CSPM for security and compliance audits across your multi-cloud environments. To decrease the load on the security operations team, you are researching how to auto-remediate some of the security violations found in low-risk environments.
Which statement is correct in this scenario?
- Netskope does not support automatic remediation of security violation results due to the high risk associated with it.
- You can use Netskope API-enabled Protection for auto-remediation of security violation results.
- You can use Netskope Auto-remediation frameworks from the public Netskope GitHub Open Source repository for auto-remediation of security violation results.
- You can use Netskope Cloud Exchange for auto-remediation of security violation results.
Correct answer: D
Explanation:
C: 1 - Mosted C: 1 - Mosted
Question 6
Review the exhibit.
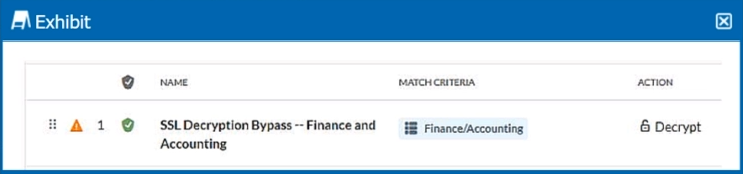
You created an SSL decryption policy to bypass the inspection of financial and accounting Web categories. However, you still see banking websites being inspected.
Referring to the exhibit, what are two possible causes of this behavior? (Choose two.)
- The policy is in a "disabled" state.
- An incorrect category has been selected.
- The policy is in a "pending changes" state.
- An incorrect action has been specified.
Correct answer: BD
Explanation:
CD: 1 CD: 1
Question 7
What are three valid Instance Types for supported SaaS applications when using Netskope’s API-enabled Protection? (Choose three.)
- Forensic
- API Data Protection
- Behavior Analytics
- DLP Scan
- Quarantine
Correct answer: BDE
Explanation:
ABE: 1 ABE: 1
Question 8
You are already using Netskope CSPM to monitor your AWS accounts for compliance. Now you need to allow access from your company-managed devices running the Netskope Client to only Amazon S3 buckets owned by your organization. You must ensure that any current buckets and those created in the future will be allowed.
Which configuration satisfies these requirements?
Correct answer: D
Explanation:
A: 1B: 1 A: 1B: 1
Question 9
You deployed IPsec tunnels to steer on-premises traffic to Netskope. You are now experiencing problems with an application that had previously been working. In an attempt to solve the issue, you create a Steering Exception in the Netskope tenant for that application: however, the problems are still occurring.
Which statement is correct in this scenario?
- You must create a private application to steer Web application traffic to Netskope over an IPsec tunnel.
- Exceptions only work with IP address destinations.
- Steering bypasses for IPsec tunnels must be applied at your edge network device.
- You must deploy a PAC file to ensure the traffic is bypassed pre-tunnel.
Correct answer: C
Explanation:
C: 2 C: 2
Question 10
Review the exhibit.
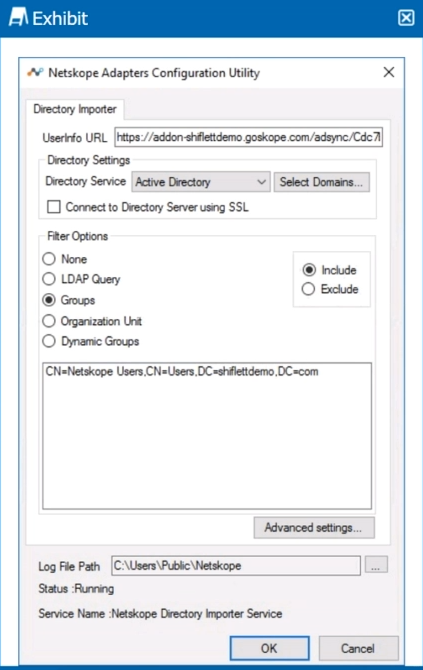
You installed Directory Importer and configured it to import specific groups of users into your Netskope tenant as shown in the exhibit. One hour after a new user has been added to the domain, the user still has not been provisioned to Netskope.
What are three potential reasons for this failure? (Choose three.)
- Directory Importer does not support ongoing user syncs; you must manually provision the user.
- The server that the Directory Importer is installed on is unable to reach Netskope’s add-on endpoint.
- The user is not a member of the group specified as a filter.
- Active Directory integration is not enabled on your tenant.
- The default collection interval is 180 minutes, therefore a sync may not have run yet.
Correct answer: BCE
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!







